Do you know what Zayka Ransomware is?
Zayka Ransomware is a variant of the malicious Cryptomix Ransomware, which is well-known because of the many other variants that include Mole ransomware, CryptoShield Ransomware, and Exte Ransomware. According to our research team, several different versions of the threat we are discussing could exist as well. Both variants should place a file called “_HELP_INSTRUCTION.TXT”, but the message within the file is different depending on the version that you are dealing with. It is easy to determine which infection has invaded your operating system because of the “.ZAYKA” extension that is attached to the files that are encrypted. Unfortunately, these files are also renamed, which might make it difficult for you to see which ones were affected. The first question you should ask yourself when you discover this mess is whether or not you have backups. If you do, you should remove Zayka Ransomware without wasting any more time. If your files are not backed up, continue reading to learn what has happened.
Different variants of the Cryptomix Ransomware are known for the smart distribution tactics. The cyber criminals behind this malware have employed various different techniques, and that is what makes it more flexible and unpredictable. It is believed that Zayka Ransomware primarily spreads via spam emails, and so you have to be extremely cautious. In the past, Mole Ransomware was spread via emails that were allegedly created by the USPS, and so similar scams could be employed for this threat. The infection does not waste time when it comes to the encryption of your files, and it is likely to initiate the process as soon as it is executed. Before that, the threat adds itself to the RUN registry to ensure that it runs even if you restart the computer. After the encryption, Zayka Ransomware creates the “_HELP_INSTRUCTION.TXT” file, and as we discussed already, two different versions exist. Although this file is not harmful, and you can open it risk-free, we recommend deleting it when eliminating the ransomware.
The first version of the Zayka Ransomware ransom note is lengthier. It tells you what happened, promises to decrypt your files, explains how to purchase Bitcoins, and warns you against decrypting files yourself. It is suggested that files can experience permanent damage if you try to decrypt them yourself. Also, it is stated that you have 36 hours to act. The first step would be to email admin@zayka.pro. This email address is represented via the shorter version of the ransom note as well. Unlike the longer version, this one includes the so-called “DECRYPT ID,” which you are expected to email for identification. So, do the creators of Zayka Ransomware have the ability to decrypt your files? They might, but that does not mean that they would. Most victims of ransomware infections report not getting anything in return of the ransom payments they make. Do you want to waste your money? If you do not, you should not pay the ransom.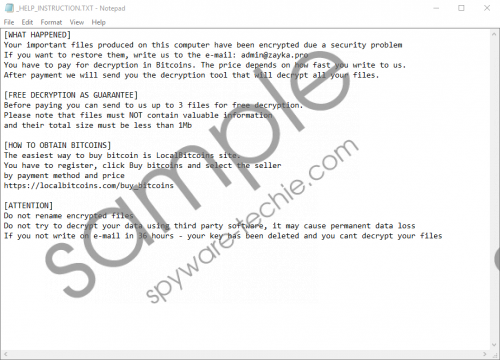 Zayka Ransomware screenshot
Zayka Ransomware screenshot
Scroll down for full removal instructions
Your virtual security is at risk, and you need to take care of this as soon as possible because the World Wide Web is crawling with all kinds of malicious infections, and they might use all kinds of methods to slither into your operating system. Without a doubt, we recommend employing anti-malware software, and if you install it now, you will have Zayka Ransomware deleted automatically. If other infections exist, they will be eradicated as well. What if you want to get rid of this infection manually? If that is your choice, you can follow the manual removal instructions below. If you encounter obstacles, use the comments section to ask questions regarding the removal process.
Remove Zayka Ransomware
- Simultaneously tap Win+R keys to launch RUN.
- Enter regedit.exe to launch Registry Editor.
- Move to HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RUN.
- Delete three {random name} values associated with the ransomware (e.g., 00FF0EBCF2F2¬, BC0EBCF2F2, and *BC0EBCF2F2).
- Simultaneously tap Win+E keys to launch Explorer.
- Enter %APPDATA% into the bar at the top to access the directory.
- Delete a {random name} executable associated with the ransomware (e.g., BC0EBCF2F2.exe).
- Empty Recycle Bin.
In non-techie terms:
Zayka Ransomware is a threat that deserves immediate removal. At the time of research, it was not possible to decrypt the files corrupted by this malware without the decryption/private key, but it is possible that a decryptor will be created in the future. The older infections from the Cryptomix Ransomware family are all decryptable. Can you recover your files by paying the ransom? Although that might be technically possible, we do not recommend wasting your money because cyber criminals are unlikely to spend their time helping you out. What we recommend is deleting Zayka Ransomware, and the sooner you do this, the better. Follow the removal guide above, or, if you are also interested in full-time protection, employ a legitimate anti-malware program.
