Do you know what Wildfire Ransomware is?
Wildfire Ransomware is a new ransomware infection that might cause many problems for you if it ever finds a way to your system. This ransomware infection was first detected on the 21st of June, 2016, so it is not very popular at the time of writing; however, our team of specialists believes that everything might change quickly. As our experience shows, users quickly understand that the ransomware infection has entered their computers because they notice new files created, see a different picture set as the Desktop background and, most importantly, they cannot access their files because the ransomware infection encrypts them all. In this case, Wildfire Ransomware will assign the .wflx filename extension to each file it encrypts, so it will not be hard to understand that Wildfire Ransomware is inside the system. Unfortunately, it will not be easy to unlock files it has locked because it is very likely that is uses the AES-256 encryption algorithm. In other words, you need to have a private key to unlock files. Even though your personal files will not be unlocked, you should hurry to delete Wildfire Ransomware from your computer as soon as possible in order to gain access to the computer and do not allow this infection to lock other files again.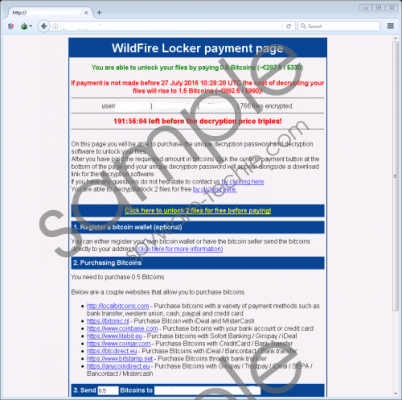 Wildfire Ransomware screenshot
Wildfire Ransomware screenshot
Scroll down for full removal instructions
Wildfire Ransomware immediately encrypts a number of files once it sneaks onto computers. Then, it creates .html and .txt files (HOW_TO_UNLOCK_FILES_README_([Unique ID]).html and HOW_TO_UNLOCK_FILES_README_([Unique ID]).txt) in directories that contain encrypted files and automatically opens them after it finishes encrypting files to make sure that users notice them. There is a possibility that your Wallpaper will be changed too because one of the components of this threat is the .bmp image (it can be found if you follow this path %APPDATA%\WildFire V1\WildFire V1\1.0.0.0\[random 5 numbers].bmp). All the new files the ransomware creates contain the ransom message, for example, the .txt file has the following text (an excerpt):
All your files have been encrypted by WildFire Locker
All your files have been encrypted with an unique 32 characters long password using AES-256 CBC encryption.
The only way to get your files back is by purchasing the decryption password!
The decryption password will cost $/€299.
You have time until {date} before the price increases to $/€999.
The ransom Wildfire Ransomware asks users to pay for the decryption key is quite small if compared to those asked by other well-known ransomware infections; however, specialists still do not recommend spending money on it because you might not even receive it after making a payment. Yes, there are many cases when users do not get anything in return after making a payment. We understand that you need your files back; however, we still suggest that you wait for the free decryption tool to be released in the future instead of transferring money to cyber crooks.
Ransomware infections are usually spread through spam emails. Wildfire Ransomware is no exception. It has been found that it sneaks onto computers when users download the attachment from the spam email that looks like a harmless .docx file and then enable MS Word macros to view the content of the .docx file. Once it is done, the ms.exe file that can be found in %HOMEDRIVE%\ProgramData\Memsys is launched and drops Wildfire Ransomware on the computers. The ransomware infection immediately creates 3 random files having .exe, .xml, and .png filename extensions in the folder that can be found in %APPDATA%\[10 random characters] to be able to work properly. Believe us; similar threats might enter your computer quickly too. To be frank, you will probably not even notice when this happens. Therefore, we suggest taking care of the system’s safety in advance by simply installing reliable security tool and keeping it enabled 24/7/365.
There are two ways to delete Wildfire Ransomware from the system. You can either delete this infection manually or go for the automatic removal. In case you decide to erase this infection yourself, you should follow our step-by-step removal guide, especially if it is the first time you are about to delete such a serious computer infection. If you are planning on erasing Wildfire Ransomware automatically, you simply need to scan your computer with a trustworthy automatic malware remover, e.g. SpyHunter.
Delete Wildfire Ransomware
- Locate and delete the .docx file you have downloaded from the spam email.
- Tap Win+E.
- Copy and paste %HOMEDRIVE%\ProgramData\Memsys in the address bar.
- Delete ms.exe.
- Go to %APPDATA%.
- Remove .exe, .xml, and .png files with random names.
- Remove the WildFire V1 folder from the same directory.
- Find and remove .html and .txt files which you will find in directories containing encrypted files.
- Empty the Recycle bin.
- Reboot PC.
In non-techie terms:
As Wildfire Ransomware has found a way to your computer, it is very likely that your system contains other unreliable programs as well. Therefore, you should scan your system with the diagnostic scanner once you have deleted Wildfire Ransomware from your PC manually. Have you erased it automatically? If so, you do not need to scan your PC again because all other infections have been erased alongside the ransomware infection as well.
