2017 is not over yet, and there is still time for a new major ransomware threat to emerge, but with only a few weeks left before 2018 begins, we have to start assessing what happened in the past twelve months. While all kinds of malicious threats were wreaking havoc this year, nothing has caused more discussions than ransomware. Unfortunately, quite a few different infections were terrorizing Windows, Android, and even Mac users all over the world. Many of them were directly targeted at big companies and government institutions, and some of them were invading home systems of regular users. Ransomware is the kind of malware that does a lot of damage, which users are unlikely to recover from. The infections from this group silently invade operating systems, encrypt files, and demand ransom payments in return for decryptors. The bad news is that ransoms are usually huge and that decryption tools are not actually offered in return. In this report, we review the most significant and important ransomware threats of 2017.
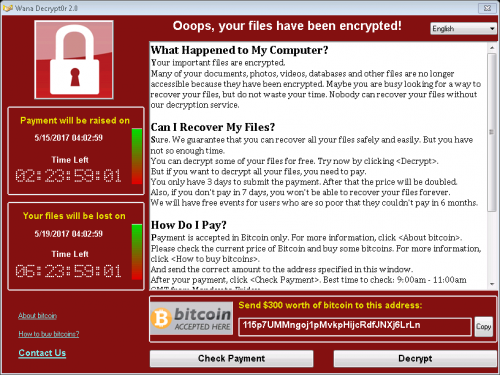
WannaCry/WanaCry/Wana Decryptor Hits 230,000 Computers
WannaCry Ransomware is, arguably, one of the most well-known infections of the last decade. When it emerged on May 12th, 2017, all news sites all over the world were covering this malicious infection. In only 24 hours, this infection managed to invade 230,000 computers in more than 150 countries. Marcus Hutchens, a security researcher from the United Kingdom, managed to stop the malicious threat, but soon after being a called a hero, he was arrested on charges of creating malware. The ransomware was targeted at companies, government agencies, health providers, and other big organizations. Ever since being unleashed, various malicious parties have attempted to exploit its name by creating lookalikes, which were found attacking Windows and Android operating systems. When the original WannaCry Ransomware was corrupting systems and encrypting files, it was demanding ransoms between 300 and 600 USD, and, in the end, someone (most likely, cyber criminals behind this ransomware) withdrew 143,000 USD from the Bitcoin Addresses used for ransom collection. Without a doubt, WannaCry Ransomware remains one of the most vicious threats of 2017.
Locky Ransomware Keeps Reinventing Itself
The infamous Locky Ransomware was created in 2016, but it was extremely active in 2017 with different versions of this malware coming and going before they could be fully analyzed and understood. The different versions of this malware use different extensions that are added to the files that are encrypted. Some include .locky, .zepto, .odin,.thor, .aesir, .loptr, .diablo6, and .lukitus. The devious Lokcy Ransomware was found to rely heavily on mass spam email attacks during the distribution. On one occasion, the launcher of the devious ransomware was spread via 23 million spam email messages in just 24 hours. On another occasion, a different mass spam email campaign was recorded (in August), when 62,000 spam email messages containing the launcher of the threat were spread. Without a doubt, this is why Locky is one of the most widely spread ransomware threats out there. Just like any other major ransomware, this threat encrypts files, but recovering them is impossible, and even if the ransom is paid, the decryptor cannot be recovered.
Petya and NotPetya: Wiper or Ransomware?
Soon after the name of the infamous WannaCry Ransomware was starting to disappear from the news headlines, an old infection, Petya Ransomware, came back into the picture. This malware was first discovered in early 2016, but different versions of it kept reemerging. The original infection, Patya, was found to infect the MBR (master boot record) to stop Windows from loading. This massive threat was targeted at bigger organizations, but it was generally believed that it was created to carry attacks on Ukrainian companies specifically. This malware came back as NotPetya Ransomware in June 2017. This malware was spread using a known vulnerability in the Windows SMB protocol using an exploit known by the name “EternalBlue.” This exploit was found to be used in the distribution of WanaCry Ransomware as well. Although this malware introduces itself as a file-encryptor that demands a ransom, malware researchers warn that NotPetya, in fact, is a data wiper that destroys the data it allegedly encrypts, which makes decryption absolutely impossible. A patch to fix the Windows SMB vulnerability (MS17-010) was released, but new versions of this devious ransomware could emerge in the future.
BadRabbit Messes with the MBR Just Like NotPetya
While new ransomware threats emerge every single day, Bad Rabbit/BadRabbit Ransomware is the newest infection out of the ones discussed in this report. This malware was discovered in October, and, at first, it was believed to be a new version of the Petya/NotPetya malware. That is not the case; however, there are many similarities between these infections. First and foremost, they can modify the MBR to show the ransom message. Unfortunately, if the MBR is corrupted, the victim not only has to worry about the encryption of their personal files but also about the functionality of the entire operating system. This threat had several different targets, but, among them, the most frequent were Ukraine and Russia, and so it is believed that the ransomware might have been created specifically for the purpose of hitting these countries. Among the companies that were hit by Bad Rabbit, we can find Kiev’s Metro, Ukraine’s Ministry of Infrastructure, and Moscow-based news agency, Interfax. Removing Bad Rabbit is a challenging process, but if an operating system is infected with this malware, it must be cleaned immediately. Paying the ransom, of course, is not recommended – just like in all other cases – because cyber criminals are not obligated and cannot be forced to provide victims with decryptors.
What to Expect in 2018
Unfortunately, it is unlikely that ransomware will stop spreading in 2018. With so many open source codes available, anyone with basic knowledge can build their own file-encrypting threats. It is likely that more ransomware infections will be created in the next year, simply because cryptocurrency – which is what cyber criminals use to collect ransoms – is gaining popularity, and, for example, Bitcoin is at an all-time high. Although it is crucial to protect files and operating systems against ransomware, one cannot forget that other threats exist as well. Malware researchers warn that instances of cryptojacking are likely to become more frequent. This could lead to the rise of malware built to silently exploit system’s resources for Bitcoin mining. Users also need to educate themselves on PowerShell-based attacks, which could lead to the infiltration of backdoor malware. The infamous WannaCry Ransomware has also shown how worms can be used to spread malware, and so malicious attackers could be using this method in 2018 as well. All in all, while you could be dealing with many dangers next year, there has never been this much information and resources at your fingertips. Use this wisely, and malware will never threaten your virtual security.
References
Chong, Z. October 25, 2017. Bad Rabbit ransomware attack bites Europe. CNET.
Comodo. New Locky Ransomware Trojan Spotted this August 2017. Comodo.
Gill, T. August 2017. Locky Ransomware Attacks Ramp Up. AppRiver Blog.
Hern, A and Solon, O. June 28, 2017. 'Petya' ransomware attack: what is it and how can it be stopped?. The Guardian.
Newman, L. H. July 1, 2017. The Biggest Cybersecurity Disasters of 2017 So Far. Wired.