Do you know what Telecrypt Ransomware is?
Telecrypt Ransomware is not your regular ransomware infection. This threat employs Telegram channels as its Command & Control server. The API of this cloud-based messenger is used to host client-server communication, and that is how the infection maintains communication with its creator. For the most part, this is used to transmit such information as your computer name, the infected system’s ID, as well as a key seed that is used for the creation of the encryption key. If Internet connection is disabled, this function is disabled as well, and that might stop the malicious threat from sending this information. Unfortunately, the threat is usually executed by opening spam email attachments, which means that Internet connection is likely to be established when the threat slithers in and communicates with cyber criminals to receive an encryption key. If the devious threat manages to encrypt your files, you do not have many options. Continue reading to learn about these options, as well as the removal of Telecrypt Ransomware.
According to our malware research team, Telecrypt Ransomware is spread via a spam email attachment, and it might represent a harmless-looking file, such as a Word Document or a PDF. If you click this attachment to open it, the ransomware is executed, and the encryption of the files begins shortly after that. The version of the ransomware that was tested in our internal lab was capable of encrypting all files with these extensions: .cd, .dbf, .doc, .docx, .dt, .jpeg, .jpg, .png, .pfd, .xls, and .xlsx. Clearly, this threat is targeting your personal documents and photos. When these files are encrypted, you will not be able to open them as you normally would. You might also find an additional extension appended to their names (e.g., “.Xcri”). When all files are encrypted, a file called “База зашифр файлов.txt” is created on the Desktop, and it lists all paths to the encrypted files. If the Internet connection is not disabled at this point, Telecrypt Ransomware proceeds to download a file called “Xhelp.exe” to %TEMP%. This file represents the ransom demands.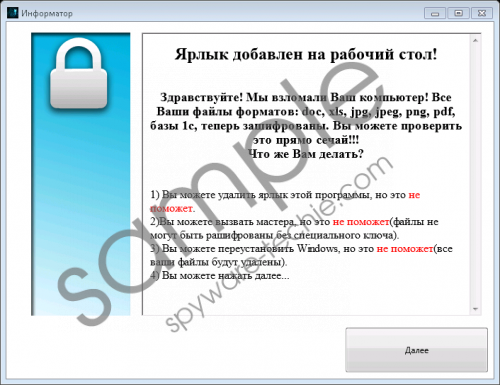 Telecrypt Ransomware screenshot
Telecrypt Ransomware screenshot
Scroll down for full removal instructions
The malicious Telecrypt Ransomware is targeted at users who speak Russian, and so it is not surprising that the ransom note is in Russian as well. The first page informs that you have no options once the files are encrypted. The information in the second page issues an apology and suggests that you should pay a ransom of 5000 rubles using Yandex or Qiwi payment systems. The last part in the ransom note asks to confirm the payment by sending your IP within three days. The message also includes a “Thank you” note for helping young programmers. Overall, if you look at the ransom note, it is clear what has happened to your files. The question is: What are you going to do about it? First, close the ransom note window and check which files were encrypted. If you realize that you have backups in an external drive or cloud storage, you do not need to worry about anything else but the removal of Telecrypt Ransomware. If you need to recover your files, you might think about paying the ransom. If you are thinking about this, remember that you might lose your savings for nothing because cyber criminals do not care about your files at all.
There is no doubt that Telecrypt Ransomware is a dangerous threat that requires elimination. Luckily, it’s not all bad news. As our tests have shown, it is quite easy to delete Telecrypt Ransomware from your operating system even if you lack experience. The main task is finding the launcher of the infections, and, considering that you might have downloaded it yourself, you should be able to find it without much trouble. If you are lost, you should not hesitate to install automated malware removal software. Another reason to install this software is the existence of other infections. Since your operating system is clearly vulnerable, security-wise, other threats might have found their way in. If you want to prevent malware from attacking you in the future, the best thing you can do is install a reliable anti-malware application.
Remove Telecrypt Ransomware
- Delete the malicious .exe launcher (the one you might have downloaded via spam email attachment).
- Move to the Desktop and Delete the files named Xhelp.exe and База зашифр файлов.txt.
- Tap Win+E to launch Explorer.
- Enter %TEMP% into the bar at the top to access the directory.
- Delete the file named Xhelp.exe (the file on the Desktop is its copy).
In non-techie terms:
Telecrypt Ransomware is an infection that can corrupt your files and force you to pay a ransom in return for their release. The problem is that no one knows if your files would be released if you paid the ransom, and that is the main reason to look at other options. Maybe there is a legitimate file decryptor that could help you? In the best case scenario, of course, you will have your files backed up. When you delete the malicious ransomware from your PC, you need to take measures to avoid the loss of files and the attacks of malware that might occur in the future. We advise setting up cloud storage to back up your files and investing in legitimate anti-malware software to guarantee full-time protection.
