The EternalBlue Exploit known by the code CVE-2017-0144 is one of those vulnerabilities that Windows users might be already familiar with. This vulnerability was patched nearly a year ago (March 2017), but it appears that not everyone got the memo about how important it was to download the necessary security patch update. The vulnerability used by the exploit was first discussed widely after the outbreak of the infamous Wana Decrypt0r Ransomware that used it to infect 230,000 computers the first day it was unleashed. The EternalBlue exploit was also linked to the proliferation of the malicious Petya 2017 Ransomware. Malicious attackers have found a new way to use the exploit: They are now spreading the clandestine Smominru miner.
According to the researchers at proofpoint.com – who worked along with abuse.ch and ShadowServer – Smominru miner (also known as Ismo) employed 25 hosts to conduct attacks using the EternalBlue exploit to create a botnet of hosts that were used solely for the purpose of mining Monero, which is a cryptocurrency on the rise. Researchers concluded that over 526,000 infected Windows hosts were added to the botnet. It is believed that most of these hosts were servers, which, of course, is the more desirable target for the attackers behind the miner because servers are more powerful and usually run without interruptions. All in all, Smominru is quite unusual. Tom Spring at threatpost.com has talked about the size of the botnet with proofpoint’s Patrick Wheeler, who pointed out that Smominru is unique because of its size and resilience. Even after the miner was sinkholed (an action when traffic is redirected from infected machines), it managed to return; even if not at full power. Another unique thing about the miner is that it uses WMI (Windows Management Instrumentation).
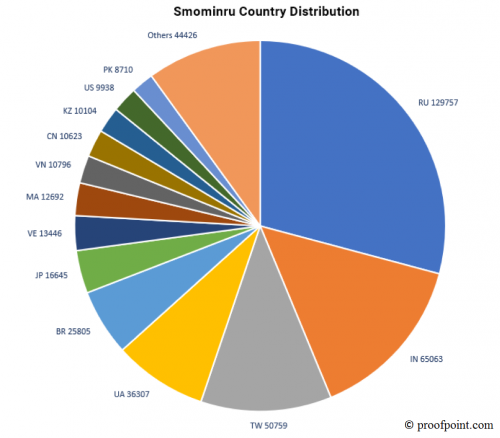
It is believed that the Smominru miner has mined at least 8,900 XMR (Monero). This number may seem small, but once it is converted to US Dollars, it is quite shocking. In early February 2018, this sum converted to nearly $1.8 million; however, at the time of the mining, it could have been anywhere from $2.8 million to $3.6 million. Based on this data, Smominru might be the most successful miner of all time. The researchers list Russia, India, and Taiwan as the countries with the highest numbers of infected hosts. Researchers at Avast have swapped India for Ukraine in their own top 3 list. Here is a chart revealing the percentage of infection.
According to the latest information, EternalBlue Exploit (CVE-2017-0144) is likely to be used along with EsteemAudit Exploit (CVE-2017-0176), which is a remote code execution vulnerability. This vulnerability has been patched in June 2017. It goes without saying that if the vulnerabilities are patched using the appropriate security updates, the systems and servers cannot be exploited by the Smominru miner. If the security updates are not installed, the backdoors are not patched, and remote attackers can implement the Server Message Block (SMB) to exploit the vulnerability and drop the miner. This is done by silently installing the Tor Browser, which is used to access hidden servers with a malware request. After that, the malware is downloaded and self-replicated. This is how the EternalBlue Exploit works. The EsteemAudit Exploit works by exploiting the Windows Smart Card component on Windows XP and Windows Server 2003.
The patch for the EternalBlue Exploit (CVE-2017-0144) vulnerability can be found HERE (for Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows R2 8.1, Windows 10, and Windows Server 2016).
The patch for the EsteemAudit Exploit (CVE-2017-0176) vulnerability can be found HERE (for Windows XP and Windows Server 2003).
All Windows security updates must be installed immediately because every single known vulnerability can be employed by malicious attackers to infiltrate malware and wreak havoc. Every Windows user can set their Windows updates to be automatic. These settings can be adjusted in the Control Panel\System and Security\Windows Update\Change settings menu.
References
Hron, M. February 2, 2018. Botnet at large: Avast blocks Smominru miner. Avast Blog.
Proofpoint. January 31, 2018. Smominru Monero mining botnet making millions for operators. Proofpoint.
Spring, T. February 1, 2018. Massive Smominru Cryptocurrency Botnet Rakes In Millions. ThreatPost.
Yan, T. May 31, 2017. A Dissection of the “EsteemAudit” Windows Remote Desktop Exploit. Palo Alto Networks.