Do you know what ShinoLocker Ransomware is?
ShinoLocker Ransomware is a ransomware simulator that was created by a security researcher Shota Shinogi. The idea behind the malicious program is that anyone can participate in its creating and understand how popular ransomware infections work. The site with the simulator claims that “The difference between ShinoLocker and real ransomware is that it never asks ransom.” It means that you can encrypt data on your computer and also decrypt it on your own and free of charge. However, if anyone can download and customize the malware, we could expect that someone will try to create a version that would demand a ransom. If that ever happens, it would be smart to know more about the infection. Thus we advise you to continue reading the article and also take a look at the removal guide below.
ShinoLocker Ransomware is currently available on shinolocker.com web page. If you are curious, you can enter the site yourself as it is safe to visit. To infect the system, you would need to click the download button and launch an executable file. As it seems, the malware should create a copy of the malicious file in the %TEMP% directory. After the system gets infected with the malicious program, it displays a separate window on the screen, which allows you to watch the progress.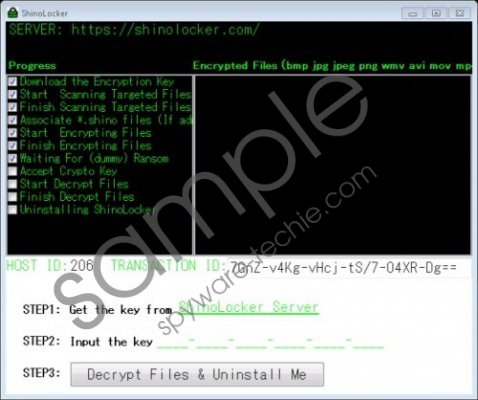 ShinoLocker Ransomware screenshot
ShinoLocker Ransomware screenshot
Scroll down for full removal instructions
All data that is locked by the malicious application should have an additional extension called .shino. Also, the files’ icons should be replaced with ShinoLocker Ransomware logo. To get the decryptor and decipher the data, the user should click on a link next to the “STEP 1: Get the key from” line on the software’s window. It redirects you to shinolocker.com where you can copy the key. All you have to do is paste it into the “Step 2” line and click the “Decrypt Files & Uninstall Me” button. Afterward, the malware should not only unlock your data but also erase itself from the system.
That is how the infection works if it comes from the official site that contains the simulator. Nevertheless, the program is written in .NET framework, which means that a person who has the right skills can see ShinoLocker Ransomware’s code and make modifications to it. As a result, a new version that might not even look like the initial one could be created. Therefore, it would not surprise us if someone with malicious intentions would use this opportunity to make some money.
The original version can be erased manually if the user deletes the infected file and its copy. Nevertheless, if the software would be modified by someone with malicious intentions such person could change the malware’s removal as well. Of course, if that part does not change, users should be still able to delete it with the instructions below. The worst part is that the altered version could look entirely different from the original ShinoLocker Ransomware. In situations when you cannot identify malware that infected the system it is best to use a reliable security tool since it can perform a system scan and detect suspicious data. In any case, we would advise users to get a trustworthy antimalware tool before anything happens. If you occasionally open suspicious files or download installers from various file-sharing web pages, it would be a good idea to consider such tools. A reliable antimalware software can warn you about malicious data and help you avoid infections.
Remove ShinoLocker Ransomware
- Launch the Explorer (press Windows Key+E).
- Locate a malicious file you downloaded yourself; it could be placed in the Desktop, Downloads, Temporary files, and other directories.
- Right-click the malicious file and press Delete.
- Navigate to %TEMP%
- Find a copy of the malicious file.
- Right-click the copy and select Delete.
In non-techie terms:
ShinoLocker Ransomware is a malicious program that was created for security researchers to demonstrate how such infections work. It is distributed through a site where you can create a unique ransomware’s version by changing the default configuration. The initial release also has a safety switch that protects user's data if he could not decrypt it successfully. The malware makes copies of files and places them in the Recycle bin, so if for some reason the user cannot decrypt data, he should still recover it from copies. However, if someone would make a ransomware that asks for ransom, such version would probably be without any safety switches. In such case, you could try the removal guide below or better yet delete the threat with an antimalware tool.
