Do you know what Shark Ransomware is?
Shark Ransomware is a type of ransomware that anyone can get their hands on and use to infect other computers and demand the victims to pay a ransom. Therefore, it falls into the subcategory of Ransomware as a Service (RaaS). It has a dedicated distribution website and is distributed as a legitimate application. However, if you were unfortunate enough and your computer became infected with it, then you have to remove it because paying the ransom may be uneconomical and unreasonable. At present, no third-party decryption tool could decrypt your files free of charge, but this is no excuse to comply with the demands of the cyber criminals.
Our security specialists have obtained a sample of this ransomware’s executable and tested it and in this description, we will overview and talk about their findings. Criminals can download this ransomware’s payload bundle from its dedicated website at Sharkproject{.}tk. This upfront distribution and marketing tactic is indeed bold, and some web browsers might block access to it on the grounds that the website is malicious. Shark Ransomware’s developers sell the license to use this malware and charge 20 % of the profits their “clients” make. The strategies and methods used to get computers infected with this ransomware may vary as they are down to the imagination of the cyber criminals that bought it. However, it must be said that its main executable must be launched manually, so the criminals need to develop a social engineering ploy to convince the victims to run the malicious executable which they might rename, of course.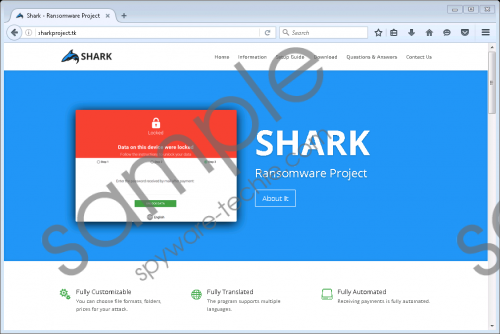 Shark Ransomware screenshot
Shark Ransomware screenshot
Scroll down for full removal instructions
The payload consists of three files that include Payload Builder.exe, Readme.txt, and Shark.exe — the main executable. Cyber criminals can customize this ransomware’s settings and select which folders and file formats to target. They can also select the specific countries this ransomware should target as well. Hence, if it infects a user in an excluded country, then the ransomware should not work, at least that is the theory presented by our analysts. However, in the event the victim meets the criteria, Shark Ransomware will begin the encryption process.
When the victim launches Shark.exe, it will create a copy of the executable and drop it in %APPDATA%\Settings. Take note that %APPDATA% is a hidden folder, and the Settings folder is also created by this ransomware. While it encrypts the files, it adds the .locked extension to the encrypted files which is an indication that the files have been encrypted. Once the encryption process is complete, Shark Ransomware will create a shortcut named UNLOCK ME that, when launched, will present you with a Graphical User Interface (GUI.) It features a polished interface and the victim can even select its preferred language from a list of 30 languages.
The process of getting your files back consists of three steps. You must first enter your email address in the provided dialog box, then purchase Bitcoins and send 0.17403411 BTC (an approximate 99.70 USD) to the provided Bitcoin address. The third step is to enter the password that you have received in the mail. Now, 99.70 USD may not look like much, but there is no guarantee that you will get the password once you have paid the ransom. Also, the encrypted files may not be worth this sum of money, so you should consider deleting this ransomware instead of complying with its demands.
If you want to delete this infection manually, then you can make use of the manual removal guide provided below. You only have to delete the two executables of which one is located in the location you ran it from and the other is dropped in %APPDATA%\Settings. Alternatively, you can use SpyHunter to eradicate it automatically. This program will also protect your PC from similar infections and malware attacks in the future.
Remove Shark Ransomware manually
- Delete the malicious executable from where you launched it.
- Press Windows+E keys.
- Enter %APPDATA%\Settings in the address box.
- Find the malicious executable (Shark.exe) and delete it.
- Empty the Recycle Bin.
In non-techie terms:
Shark Ransomware is distributed as a Ransomware as a Service, and this means that anyone can get it infect the computers of unsuspecting Internet surfers. It is set to encrypt your files and demand that you pay a ransom for the password that would decrypt them. You can try paying the ransom, but there is no guarantee that you will get your files back. Therefore, we advocate for its removal.
