Do you know what Shadow Ransomware is?
Shadow Ransomware appears to be capable of encrypting almost all data located on the infected computer, except the files belonging to Windows. It means if the malware manages to enter your system you might lose all of your data unless you have any copies of it on cloud storage, removable media devices, or other places that could not be affected by this threat. However, before recovering any data, it would be advisable to secure the system by erasing the malicious program. It might be easier to do so with a reputable antimalware tool, but if you think you can manage manual deletion, you could scroll below the article and follow our provided removal guide. As for users who have not decided yet what to do, we recommend continuing reading this report. Further, in it, we will explain how Shadow Ransomware might be distributed, its working manner, and other essential details.
To begin with, we would like to talk about Shadow Ransomware’s distribution. Our computer security specialists think it should enter the system together with some suspicious recently downloaded data. For instance, it could be an email attachment you got with Spam emails, and unreliable setup wizard acquired from torrent or other questionable file-sharing web pages, and so on. Whatever it was, we advise our readers who encountered this malicious program to learn from their experience and be more cautious the next time. Instead of launching suspicious data immediately we would recommend scanning it with a reliable antimalware tool. Opening potentially malicious files right away could infect the system same fast, but scanning them may allow the user to learn of their malicious nature and as a result, protect the computer or in this case save lots of data from ruin.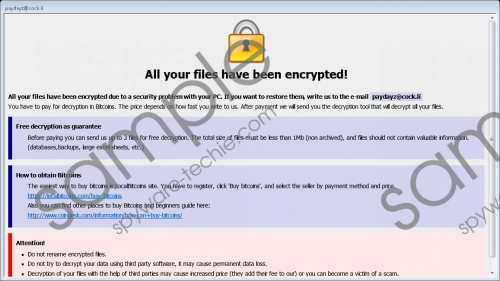 Shadow Ransomware screenshot
Shadow Ransomware screenshot
Scroll down for full removal instructions
Shadow Ransomware can be easily recognized from the specific extension it leaves at the end of every of its encrypted files. Our specialists say some parts of the extension might vary, but more or less it might look something like this .[paydayz@cock.li]-id-556.shadow. The worst part is the malicious program may encrypt both private and program data. In other words, most of the programs that do not belong to the operating system should not work anymore, and so the user has no other choice but to reinstall all of them. As for the private files, the situation is more difficult because the only way to get them back without a decryption tool is replacing encrypted files with copies from uninfected source, e.g., flash drives.
Furthermore, some of you may have also considered paying the ransom. The reason we advise against it is that there are no actual reassurances the victim will receive the promised decryption tool, even if the malware’s creators “guarantee” it in their ransom note. The truth is once you pay you cannot take your money back and if you do not receive the decryption tool, there will be no one to complain about it too. It is unknown how much is the ransom as the information on Shadow Ransomware’s ransom note only explains how to purchase Bitcoins or contact the hackers behind the threat. In any case, whatever the sum is we do not think it would be wise to risk losing it, but naturally it is something only the victims of this malware can decide.
Users who do not plan on making the payment should erase Shadow Ransomware with no hesitation. There are two ways one can achieve this. First of all, you could have a look at the removal guide placed at the end of this text and try to get rid of it manually. Provided, it looks a bit complicated, or you want to make sure there are no other threats on the system you could perform a full system scan and eliminate the malicious program along with any other detections by clicking the deletion button. Users who pick this option should install a new and reputable antimalware tool because if they had one already, it was most likely encrypted when the computer got infected.
Erase Shadow Ransomware
- Press Ctrl+Alt+Delete simultaneously.
- Pick Task Manager.
- Take a look at the Processes tab.
- Locate a process belonging to the malicious program.
- Select this process and press the End Task button.
- Click Windows Key+E.
- Navigate to the suggested paths:
%TEMP%
%USERPROFILE%Desktop
%USERPROFILE%Downloads - Search for a file that was launched when the system got infected.
- Right-click the malicious file and select Delete.
- Then go to %APPDATA% and delete payday.hta.
- Leave File Explorer.
- Restart the computer.
In non-techie terms:
Shadow Ransomware is a dangerous file-encrypting threat you could infect your computer with after opening suspicious data. Sadly, usually, users realize what has happened only after the malware has already encrypted their data. That is because it can work silently in the background without drawing any attention. Nonetheless, later on, the malicious program should place a ransom note or perhaps some copies of it in most visible places, e.g., user’s Desktop. The message on it should demand to pay a ransom and promise you will receive a decryption tool in no time. No matter how convincing this message may sound, it would not be advisable to put up with any demands, because you might end up being tricked and so could lose your savings for nothing. Thus, if an emptier wallet does not sound right, we encourage you not to take any chances and eliminate the threat. To achieve this, you can follow the removal guide located above or employ a reputable antimalware tool of your preference.
