Do you know what SATANA Ransomware is?
SATANA Ransomware is not your regular ransomware infection. Just like other threats in the family, including Bart Ransomware or TeslaCrypt Ransomware, it demands for a ransom payment after encrypting personal files. What is unique about this infection is that it is capable of changing the Master Boot Record (MBR). Right as we discovered this, we immediately linked this malicious infection to two other infamous ransomware threats that act virtually the same. These threats are Petya Ransomware and Mischa Ransomware, and they were found overwriting boots files responsible for loading MBR. Unfortunately, this means that you will have to deal with two different problems: the encryption of your files and the corruption of MBR. If you think that everything can be solved by removing SATANA Ransomware, you are completely wrong. Continue reading to learn more about this.
You might not notice when SATANA Ransomware enters your operating system. If it is downloaded by a Trojan, you will be completely oblivious, and, if you execute it by opening a spam email attachment, you might not expect for a malicious ransomware to be unleashed. There could be many different ways for this threat to enter your operating system, but it is very likely that you will launch it yourself without realizing it. Once launched, this threat copies itself to the %TEMP% directory, and this is where is it run from. Once run, the encryption process begins, and all photos and documents found on your PC are encrypted. Right after this, text files (!satana!.txt) are dispersed all over your computer to represent the instructions that you are expected to follow for supposed decryption of your files. The same instructions are also represented via the wallpaper that the ransomware sets after encryption. Do NOT restart your computer after discovering this mess. Due to the changes in the MBR, Windows will not launch after restart.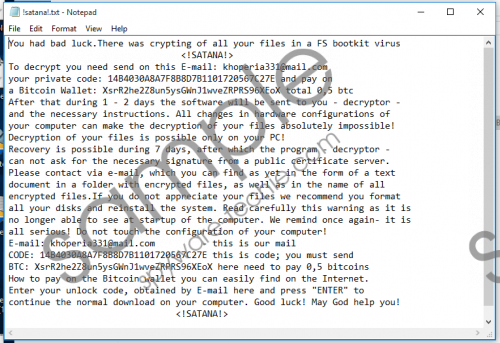 SATANA Ransomware screenshot
SATANA Ransomware screenshot
Scroll down for full removal instructions
According to the SATANA Ransomware instructions, your files were encrypted by the FS bootkit virus. These instructions include a private key that you need to provide to cyber criminals by contacting them via khoperia331@mail.com. Additionally, a Bitcoin wallet address is provided that you are expected to use to pay the ransom of 0.5 Bitcoins. Although the number might seem small, at the moment, it converts to 338 USD or 305 Euro. The message also suggests formatting your disks and reinstalling the operating system as an alternative to paying the ransom. Of course, if you do that, you will lose all chances of decrypting your files. In fact, your files will be erased for good. However, if you pay the ransom, you are at risk of being scammed. According to our research, a working third-party decrypter does not exist right now, but it is possible that it will be developed in the future. Of course, it is also possible that it will not.
As our research team has discovered, the removal process consists of repairing the Mater Boot Record and deleting SATANA Ransomware components. If you choose to follow this method, only follow it once you know what you want to do with your files. Once you repair the MBR, you will no longer have the chance to decrypt your files. The instructions below show how to perform this complex task. Afterward, you need to restore your regular wallpaper, delete the main launcher, as well as the copy in the %Temp% directory, and the text file that might be copied to every location containing encrypted files. Finally, employ a trusted anti-malware tool to ensure full-time protection against ransomware and other types of malware. If you have any questions about the removal process, feel free to start a discussion via the comments section below.
Remove SATANA Ransomware
- Insert the Windows installation disk into the CD/DVD-ROM and restart your computer.
- Choose Boot in the Setup Utility menu.
- Choose CD-ROM Drive and tap Enter.
- Once Windows start, follow the instructions below.
Windows XP
- In the Welcome to Setup screen tap R on the keyboard to access Recovery Console.
- Type 1 after Which Windows installation would you like to log onto and tap Enter.
- Enter the password and tap Enter.
- Enter fixmbr after C:\Windows> and tap Enter.
- Type Y to confirm the writing of a new MBR and tap Enter.
- Wait for the fixmbr utility to repair Master Boot Record.
- Remove the CD, enter exit, and then restart your computer.
- Delete the malicious components of the devious ransomware.
Windows Vista or Windows 7
- Select the preferred Language, Time, and Keyboard, and click Next.
- Click Repair your computer, choose your operating system, and click Next.
- Select Command Prompt to launch the utility.
- Enter bootrec /fixmbr and tap Enter.
- Enter bootrec /fixboot and tap Enter.
- Enter bootrec /rebuildbcd and tap Enter.
- Remove the CD after the confirmation message shows up.
- Enter exit and restart your computer.
- Delete the malicious components of the devious ransomware.
Windows 8 or Windows 8.1 or Windows 10
- Select the preferred Language, Time, and Keyboard, and click Next.
- Click Repair your computer and then click Troubleshoot.
- Choose Command Prompt to launch the utility.
- Enter bootrec /fixmbr and tap Enter.
- Enter bootrec /fixboot and tap Enter.
- Enter bootrec /scanos and tap Enter.
- Enter bootrec /rebuildbcd and tap Enter.
- Remove the CD after the confirmation message shows up.
- Enter exit and restart your computer.
- Delete the malicious components of the devious ransomware.
In non-techie terms:
There is little you can do once SATANA Ransomwareinvades your operating system. The strength of this ransomware is that it encrypts files without leaving a way out. Are you thinking about paying the money that is requested from you? Well, that could be the worst idea, considering that there are no guarantees that this would work. In fact, you might lose your money for nothing in return. If you take the risk and, by some miracle, your files get decrypted, do not forget to delete SATANA Ransomware from your operating system as soon as possible. If you are having trouble fixing the Master Boot Record or eliminating the elements of the ransomware, use the comments section below to ask questions.
