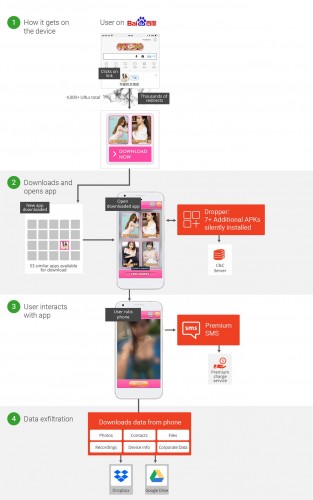
Cyber criminals continue developing Android malware, and this is not something very surprising because the total number of people using Android is growing, and Android is still considered one of the most popular operating systems available. Researchers at the security firm Wandera based in the United Kingdom have recently discovered new sophisticated Android malware named RedDrop that is being distributed inside 53 useful-looking Android applications. No, you will not find in on Google Play because it is promoted exclusively on third-party app stores. Applications promoting RedDrop include picture editing tools, calculators, language learning tools, and adult-themed apps. The malicious application was first detected on mobile phones of employees working in several consultancy firms, but there is no doubt that they are not the only ones who encountered this Android malware. Researchers have observed that this infection is the most prevalent in China. Since the official Google Play store does not work there, users use search engines like Baidu to find mobile applications and thus install apps promoting RedDrop without even realizing that. This is considered the main distribution method used to spread RedDrop malware.
It is unclear how many Android devices have already been affected by RedDrop malware, but specialists at Wandera claim that this infection is becoming more and more prevalent. According to them, this is not something very surprising because RedDrop malware is promoted via malicious advertisements on Baidu, a popular Chinese search engine used by thousands of people to perform web searches. One of the first apps carrying RedDrop was detected when a user clicked on an advertisement found on Baidu and ended up on huxiawang.cn, which is considered “the primary distribution site for the attack.” The landing page contained content encouraging the user to download one of 53 “beneficial” applications containing RedDrop malware. It has also been observed that cyber criminals behind this threat use the so-called “content distribution network (CDN)” consisting of more than 4000 domains to distribute applications promoting RedDrop malware. As a consequence, users who ended up on huxiawang.cn experienced series of redirects before being presented with the download itself. Without a doubt, this is a tactic used to avoid malware detection.
Once users install a RedDrop-infected app on their devices and agree with permissions the app asks, malware starts working immediately and sends some information about the affected device to its C&C server. Then, it downloads seven other components from various servers without the user’s knowledge. These are mainly Android application packages (APK) with different functionalities. It seems that the main goal RedDrop malware tries to achieve is to subscribe users to premium SMS services. These text messages are sent to premium services every time infected apps are used. For instance, an adult-themed app CuteActress sends an SMS message to a premium service each time the user “rubs” the screen. What is more, RedDrop malware might be used to steal information from users’ Android devices, specialists say. It is capable of accessing and stealing the following details:
- Locally saved files, including photos, contacts, and images
- Live recording of surroundings
- Device-related information, including IMEI and IMSI
- SIM-related information, including MNC and MCC
- Application data
- Information about Wi-Fi networks
The recorded information is sent straight to Dropbox and/or Google Drive folders that belong to cyber criminals behind malware.
According to researchers who have analyzed RedDrop, it is very likely that the malicious application collects personal details about the user and records audio just in case its developer might want to blackmail some victims, e.g. rich people or politicians. It is, surely, not its primary goal. As mentioned, RedDrop seeks to subscribe users to premium services above all.
Even though RedDrop is getting more and more prevalent, it does not mean that users can do nothing to prevent it from entering their Android devices. Security specialists have three pieces of advice applicable to both Chinese and non-Chinese Android users. First, set your device not to allow the installation of third-party software. Second, do not root the Android device yourself. Third, check permissions of apps you are going to install twice before actually doing that. We also want to add that it would be smart to have security software enabled on the device 24/7/365.
References:
Campbell, N. RedDrop: the blackmailing mobile malware family lurking in app stores. Wandera Blog
Cimpanu, C. New RedDrop Android Spyware Records Nearby Audio. BleepingComputer
Free stock photos in one place. Pexels
O’Donnell, L. Sophisticated RedDrop Malware Targets Android Phones. ThreatPost