Do you know what Razy Ransomware is?
Razy Ransomware is a recently discovered infection that has some similarities with the infamous Cerber Ransomware. However, these two ransomware’s are not identical and in this article, we will discuss the peculiarities of this new infection. However, before we go any further, please note that we advocate for its removal. You cannot pay the ransom because it does not save the private decryption key. So you are stuck with your files being encrypted. A third-party decryptor is your only change at getting your files back, but it has yet to be created and due to this ransomware’s strong encryption it is unlikely that it will ever be created.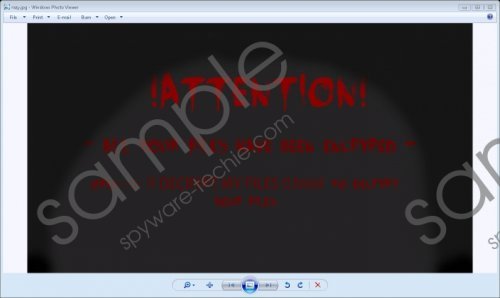 Razy Ransomware screenshot
Razy Ransomware screenshot
Scroll down for full removal instructions
Our security analysts have obtained this ransomware’s sample at the end of July of 2016. Hence, there not much information about how this infection is being disseminated. Researchers speculate that this infection is being included in malicious email attachments and distributed via email spam. The email spam can be disguised to masquerade as invoices, receipts and other types of informative emails. Usually, the emails say that you owe money for unpaid services and so on. However, the key similarity almost all of those emails have is that they feature an attachment that can come in the form of a .Zip, .Rar or some other type of archiving file format. Our malware analysts say that Razy Ransomware does not copy itself when it is launched, so it does not have to run in the background as its main executable becomes obsolete after the encryption is complete. Still, if you run it for a second time, then it will encrypt all new unencrypted files.
When you launch Razy Ransomware’s executable, it creates and places a file named css.vbs on your computer’s desktop. This file’s purpose is to play a recording that says that "Your documents, photos, databases and other important files have been encrypted." The recording is set to repeat ten times and a recording saying "Attention! Attention! Attention!" is set to play only once. In addition, this ransomware creates a file named index.html that features two links. One of them is www.lolololololol[.]de. This link does not work. The other link that we cannot post spears to be an advertisement for a mobile website developing service. The last file that this ransomware creates is named razydecrypt.jpg. It is an image file that is set as your computer’s desktop wallpaper. This image says that you have to open index.html. Our researchers have found that Razy Ransomware demands that you pay a 50 EUR ransom, but there is no way you can pay it. Moreover, even if you paid it, you would not be able to decrypt the files because this ransomware does not create a private decryption key that is usually sent to the Command and Control server and is necessary to decrypt the public key.
This ransomware uses the AES encryption algorithm, and it appends the file name with an additional .razy extension. Furthermore, it randomizes the file names, making it difficult to identify particular files. In any case, the files are ruined permanently, so there is no use in trying to save them on a flash drive or anywhere else for that matter.
In summary, Razy Ransomware is a highly malicious application that can encrypt your files and demand that you pay a ransom for the decryption key. The problem is, however, that there is no way you can pay the ransom and the decryption key is not even generated. Therefore, the only reasonable solution is to remove Razy Ransomware. You can use the instructions provided below or SpyHunter, our recommended antimalware application.
Removal Guide
- Find and delete the extracted executable.
- Then, find and delete css.vbs, razydecrypt.jpg, and index.html from the desktop.
- Empty the Recycle Bin.
- Done.
In non-techie terms:
Razy Ransomware is yet another infection set to extort money from you as it encrypts your files and demands that you pay a ransom. However, you cannot pay the ransom and the cyber criminals cannot give you the decryption key because this malware does not generate a decryption key. Therefore, our malware analysts recommend that you delete it form your PC as soon as you can.
