Do you know what Oled Ransomware is?
If some part of the data on the computer was suddenly marked with .[black.mirror@qq.com].oled extension, you most likely accidentally infected the system with Oled Ransomware. The malicious program uses AES encryption algorithm to encipher valuable files and take them as hostages. In exchange of a tool that could decrypt user’s data the cyber criminals behind this threat demand for ransom. Nevertheless, we would advise you not to put up with any demands since you could end up losing your money too and not just files. It is crucial that Oled Ransomware is eliminated as fast as possible because the malicious program can boot with the system and keep enciphering files you create afterward. More experienced users could try erasing it according to the removal guide placed below, while for less experienced users we would recommend using a reputable antimalware tool. For more information about this vicious threat have a look at the full report.
To begin with, we should say, we cannot be one hundred percent sure it is the only way the malware is being spread, but for now, it looks like it travels with malicious Spam emails. Thus, it is more likely that the system could get infected if the user carelessly opens suspicious files sent via email and does not have a reliable security tool to guard the system against such threats. Therefore, users who do not wish to become victims of Oled Ransomware’s or other malicious programs alike should take extra precautions with data received with Spam or any files sent by someone the user is not familiar with. The infection does not waste any time as it quickly makes a copy of its installer right after the user launches it.
What’s more, before starting the encryption process the threat may also make some changes to the Windows Registry. Apparently, the malware may create a couple of CLSID type value names in the Run and RunOnce keys found in the HKCU\Software\Microsoft\Windows\CurrentVersion location. Oled Ransomware’s programmed the application to act this way so it would be opened automatically when you restart your device. After enciphering files in the targeted directories, the infection should keep checking these locations for new data and if such files appear the threat should encrypt them as well. The good news is it does not target all data on the device. According to our researchers who tested the ransomware themselves, the malware is only after files in the C: disk except for folders in the C:\Windows and C:\Program Files directories. In other words, if you have two drives on the computer and you keep your valuable files on the second one (e.g. D:), you may receive little damage.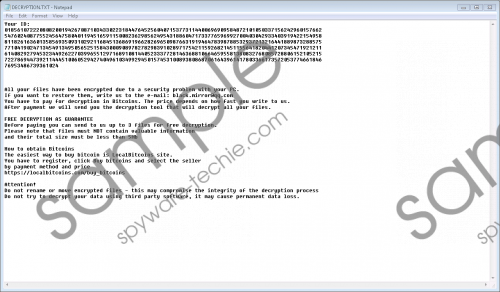 Oled Ransomware screenshot
Oled Ransomware screenshot
Scroll down for full removal instructions
The last malicious program’s action is adding a text document called DECRYPTION.txt and its copies in all the places where enciphered files are. No doubt, the file is the malware’s ransom note since it has the basic instructions on how the victim should behave, e.g. write the cyber criminals via email, purchase Bitcoins, not attempt to erase the infection, and so on. If you contact the Oled Ransomware’s creators, they will most likely demand you to pay a ransom. We cannot say how much they could ask, but we advise users not to gamble with their savings. People who create such threats do not care about the consequences of their actions; all they care about is how to extort money from you and who can promise they will bother to send the decryptor to each victim after they already have the money.
Lastly, we would like to stress it again how crucial it is to delete the malicious program before the user places any new files on the computer as they could be enciphered too. Hopefully, the removal guide placed below this text will help users achieve this task with no trouble. However, if you do not think you can handle Oled Ransomware on your own, we advise employing a reputable antimalware tool that could do all the job for you. Such a tool might be a valuable investment as it could help you keep the system safe in the future.
Eliminate Oled Ransomware
- Press Ctrl+Alt+Delete to open Task Manager.
- Look at the Processes tab and identify a process related to the malware.
- Mark it and press End Task to kill it.
- Close the Task Manager and press Windows Key+E.
- Go to Downloads, Temporary Files, Desktop, or other locations where the infection’s installer might have been downloaded.
- Select the installer and press Shift+Delete.
- Find this path: C:\Users\User\AppData\Roaming
- Search for the malicious program’s copy, e.g., 2sv_host.exe.
- Select it and press Shift+Delete.
- Use Shift+Delete to erase all DECRYPTION.txt documents.
- Close the Explorer and press Windows Key+R.
- Type Regedit and press Enter.
- Locate the following paths:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run
HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce - Find value names related to the threat, e.g., {A7U9A446-E2BB-D5EC-DG1B-EE2D64E10607}, one of its value data should point to C:\Users\[username]\DECRYPTION.TXT and the other one’s value data should point to the path where the infection’s copy was placed.
- Right-click the described value names and select Delete.
- Close the Registry Editor and empty your Recycle bin.
In non-techie terms:
Oled Ransomware is a malicious application that is programmed to encipher particular files with the AES encryption algorithm. The only way to decipher such data is with the help of a decryptor and a unique decryption key. The problem is both of these components are reachable only to the malware’s creators and in exchange for them they demand their victims to pay a ransom. Provided you do not like the possibility of being tricked and losing your savings in vain, we urge to pay no attention to the ransom note and get rid of the infection before it enciphers more data. To make this easier for you, we placed a removal guide showing how to deal with it manually above this text.
