Do you know what Nm4 Ransomware is?
The successful entrance of ransomware usually means that personal files are no longer possible to open. The same can be said about the Nm4 Ransomware entrance too, so if you cannot access pictures, documents, and media files, it might be a sign that this ransomware infection has sneaked onto your computer successfully. Since all ransomware infections act the same, i.e. encrypt files, check the extensions these files you cannot access have. If .NM4 (e.g. picture.jpg.NM4) is appended next to the original extension of every file, there is no doubt that Nm4 Ransomware is the one that should be blamed for locking them. The motive behind this is getting easy money from users – it is the only reason ransomware infections are developed so actively these days. Cyber criminals know that users will not send them money voluntarily, so they force them to make a payment by creating malware locking personal files. Once a ransomware-type infection enters the system and encrypts personal data, users get an offer to purchase an expensive private key ransomware developers have. Well, at least they claim to possess it. You have understood correctly – users cannot know whether cyber criminals behind Nm4 Ransomware have the private key and are ready to send it to them, so sending the required money might be of no use. To put it differently, users might not get the private key to unlock their files, and, without a doubt, cyber criminals will not send their money back either.
Nm4 Ransomware is one of those crypto-threats, but it does not encrypt all files it finds on the affected computer. For example, it leaves files with such extensions as .bat, .dll, .exe, .ini, .lnk, .msi, and .scf unencrypted. Additionally, it does not lock any files in %APPDATA% and %WINDIR% directories and does not touch such files as MSDOS.SYS, PAGEFILE.SYS, and NTUSER.DAT. Evidently, it has not been developed to ruin the system, but it surely encrypts personal files like images and documents. After it does that, it drops Recovers your files.html in every folder containing encrypted files. This file is a ransom note explaining how users can get their files back. First of all, users are told that their files have been encrypted using AES-256 and RSA-2048 ciphers. Then, they are told to open one of the provided links (https://3fprihycwetwk2m7.onion.to/ or https://3fprihycwetwk2m7.onion.link/) to “proceed with the purchase.” Users who open any of the links are asked to enter the unique key provided for them. Once they do that, a page Home is opened. It tells users that they have to send a “donation” of 4 Bitcoin (~6360 USD) to get the private key to decrypt files. Cyber criminals promise to send a download link as soon as they receive money, but, to be frank, there are no guarantees that this will really happen, so transferring such a large amount of money to them is not a very clever decision. Unfortunately, users who decide not to send money to cyber criminals should be aware of the fact that they might never get their files back because only those users who back up their files periodically could recover them.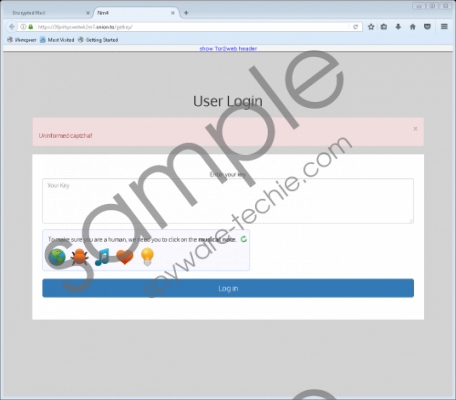 Nm4 Ransomware screenshot
Nm4 Ransomware screenshot
Scroll down for full removal instructions
Our team of experienced specialists says that it is still quite hard to say how Nm4 Ransomware is distributed since it is not prevalent; however, they are sure that it enters computers illegally like other ransomware-type infections do. Users usually contribute to their entrance without even realizing that. For example, they open malicious attachments spam emails contain. It is one of the main ways how ransomware infections enter computers, but there is no doubt that other methods might be employed to spread them too.
Users delete Nm4 Ransomware from their computers expecting that their files will be unlocked, but it is not true. Of course, it is still a must to delete this threat from the system because the encryption of files might be triggered again by opening the malicious file accidentally. Use the manual removal guide provided below this article to delete this ransomware infection from your computer.
Delete Nm4 Ransomware
- Launch the Windows Explorer (tap Win+E).
- Open %USERPROFILE%\Downloads.
- Delete suspicious files.
- Open %USERPROFILE%\Desktop.
- Remove malicious files, if you find them there.
- Empty the Recycle bin.
In non-techie terms:
Ransomware infections are extremely prevalent these days, so you might encounter a new ransomware again if you do not do anything to ensure the maximum protection of your system. What security specialists expect users to do is to install security software. Additionally, they say that users should not download programs from suspicious third-party pages because malware is often presented as useful software on them. Finally, users should stay away from spam emails because untrustworthy software often travels in them as a decent-looking attachment.
