Do you know what Mr.Dec Ransomware is?
If your operating system is not protected, Mr.Dec Ransomware is one of the many infections that could try to slither in. Using vulnerable RDP connections and various other security backdoors, this dangerous infection can invade the operating system without alerting the victim. Once in, it can encrypt hundreds and thousands of personal files, but, of course, that depends on what kind of data you keep on your computer. More and more Windows users rely on cloud storage and external drives to store their files, and if you are in the same boat too, it is unlikely that the malicious ransomware can intimidate you. Without a doubt, if malware has corrupted your personal files, and you do not have backups for them, you might be facing a huge problem. The bad news is that you cannot recover data by removing Mr.Dec Ransomware. The good news is that you can successfully delete this threat even if you are inexperienced.
When Mr.Dec Ransomware encrypts files, it attaches the “[ID]{unique ID code}[ID]” extension to all of them. The {unique ID code} part of the extension, of course, represents a combination of characters that is unique to every victim. If you discover this extension, there is no doubt that your personal files were corrupted. To achieve this, the infection employs a special AES encryption algorithm, and the key is most likely to be downloaded from a remote server upon the execution of the threat. A decryption key must be created along with the encryptor, and it should be sent back to a remote server so that victims could not discover and use it to recover their files for free. Unfortunately, at the time of research, it was not possible to decrypt files corrupted by Mr.Dec Ransomware unless the decryption key was obtained. That means that the only thing most victims can do is remove the infection.
According to our research, Mr.Dec Ransomware creates a copy of itself after execution. If the threat is executed successfully, the original launcher is deleted, and the threat operates using an .exe file in the %WINDIR% directory. The name of the file is “wincmd.exe,” but, of course, we cannot guarantee that it will be the same on your computer. In the same directory, you should find a file named “DECODE KEY.KEY,” and this file represents the unique ID code that we have already discussed. The file is created because the creator of the ransomware wants you to send it to them. This demand is made via a file named “Decoding help.hta,” and you should find it everywhere where encrypted files exist. According to the message in the file, you must send the .KEY file to shine2@protonmail.com or shine1@tutanota.com. If you contact cyber criminals, they will then send you instructions on how to pay a ransom for a decryptor that, allegedly, would restore all encrypted files. Remember that Mr.Dec Ransomware was created by criminals who cannot be trusted, which is why paying the ransom is not recommended.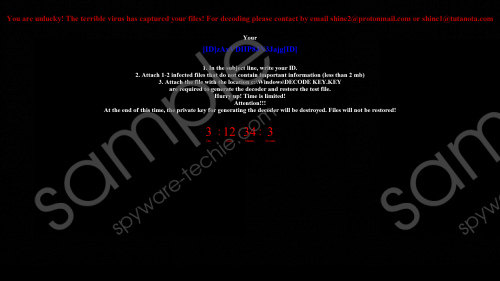 Mr.Dec Ransomware screenshot
Mr.Dec Ransomware screenshot
Scroll down for full removal instructions
The window via which the ransom note is shown can be launched in full-screen mode, but it does not lock the screen, and you can press Alt+F4 key combination on the keyboard to close it. Once you do that, you need to delete Mr.Dec Ransomware, and you can do it manually (see the instructions below) or using a tool that was built for the task. Although you might be tempted to erase the threat manually, you need to think if you will be able to secure your operating system yourself. If you will not, installing a reliable anti-malware tool might be your best option. When it comes to personal files, if you are unable to recover them, take this as a lesson to take better care of personal data in the future. Remember that keeping backup copies of your most sensitive files can be extremely helpful.
Remove Mr.Dec Ransomware from Windows
- Simultaneously tap keys Alt+F4 to close the ransom note window.
- Simultaneously tap Win+E to access Explorer.
- Type %WINDIR% into the field at the top of Explorer.
- Delete the files named DECODE KEY.KEY and wincmd.exe.
- Type %HOMEDRIVE% into the field at the top.
- Delete the file named Decoding help.hta.
- Simultaneously tap keys Win+R to launch RUN.
- Enter regedit.exe into the field to launch Registry Editor.
- Go to HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
- Delete the value named search associated with the malicious .exe file.
- Delete the value named unlock associated with the .HTA file.
- Empty Recycle Bin and then do not forget to run a full system scan.
In non-techie terms:
If Mr.Dec Ransomware has invaded your operating system, it is a sign that it was not protected reliably. This is something you need to keep in mind as you move on with the removal process. If you choose to delete the threat manually, you can have your system cleaned, but that might be a temporary fix because unguarded systems are targeted by malicious infections all the time. Now, if you employ an anti-malware program, it will automatically delete Mr.Dec Ransomware and reinforce Windows protection to ensure that malicious infections do not bother you again. Unfortunately, we cannot promise you that you will be able to restore the encrypted files. Cyber crooks might offer you a decryption tool for a certain price, but we do not recommend paying it, and a free decryptor does not exist at the moment. If you do not want to risk losing your files in the future, we suggest backing them up using cloud storage or external drives.
