Do you know what Microsoft Decryptor Ransomware is?
Even though Microsoft Decryptor Ransomware has Microsoft in its name, it does not mean that it is associated with that company in any way. This malware was developed by an unknown person, or several people and its objective is to encrypt the files on your PC and demand that you pay a ransom. However, we recommend that you remove it instead of complying with the demands because there is no guarantee that you will get the decryption software/key once you have paid. We invite you to read this short description which contains the most important information presented in simple terms.
Ransomware is a type of malware that is designed to infect your computer without your knowledge and its developers use clever yet deceptive tactics to achieve this. Email spam has proven to be effective distribution channel but it requires the potential victim to open the email attachment manually to initiate the infection. Therefore, ransomware developers started using exploit kits that use various vulnerabilities to infect a computer automatically, effectively eliminating the victim from the chain. This particular ransomware is distributed using the Angler Exploit Kit. This exploit kit is embedded in hacked websites and injects malicious JavaScript or HTML content, and when you interact with this content, Microsoft Decryptor Ransomware will infect your computer. This method was proven to be effective by multiple infections including this particular program’s clones called UltraCrypter Ransomware and CryptXXX Ransomware. Indeed, Microsoft Decryptor Ransomware comes from a developer that has already released other ransomware-type software. This newest release does not differ much but our researchers have found that even this program can have several versions that act a bit differently. So let us take a look at its functionality.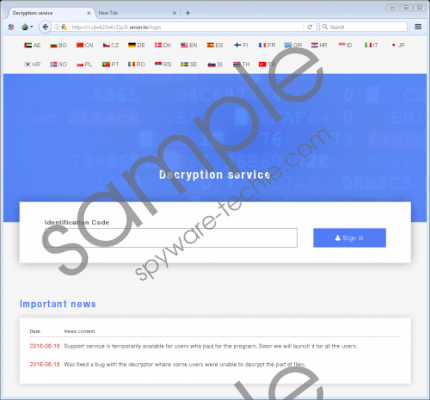 Microsoft Decryptor Ransomware screenshot
Microsoft Decryptor Ransomware screenshot
Scroll down for full removal instructions
Microsoft Decryptor Ransomware is an unconventional ransomware because it does not have an executable (.exe) file. The developers decided to use a Dynamic-link Library (.dll) file. If the infection was successful, this ransomware creates a randomly named CLSID folder (e.g. {C3F31E62-344D-4056-BF01-BF77B94E0254}) in %TEMP% and drops the .dll file in that folder. Furthermore, it copies the rundll32.exe found in %WINDIR%\SysWOW64 or %WINDIR%\System32 (depends on your operating system’s architecture) to the randomly named CLSID folder and renames it svchost.exe. This file is legitimate, but this ransomware uses it to launch its .dll file. Note that this file is also randomly named, but it was named api-ms-win-system-softpub-l1-1-0.dll in the sample tested by our malware analysts.
After successfully performing the actions described above, this ransomware runs in standby mode for 15-60 minutes (depending on the version the time varies) and then begins encrypting certain file types. This ransomware was designed to encrypt hundreds of file types, but we would like to point out that it targets file formats that contain personal information such as documents, images, videos, audio, and so on. This ransomware strives to encrypt the most valuable information with a unique RSA-4096 encryption algorithm. Unfortunately, there is no way to crack this encryption using third-party software at the time of this article. However, malware researchers may find ways to break it.
Some versions of Microsoft Decryptor Ransomware feature a lock screen that prevents you from using your computer. However, when you hold down Ctrl+Alt+Delete and restart your computer, the lock screen is not initiated. The lock screen doubles as a ransom note but the versions that do not have the lock screen create .bmp, .html, and .txt files that feature the ransom note and other less relevant information such as how to purchase Bitcoins and send them to the cyber crooks. The cyber criminals want you to pay a ransom of 0.4 BTC, which is 266 USD. However, if you do not meet the deadline of one hundred hours, then the payment will increase to 2.4 BTC (1600 USD.) In any case, that is a significant amount of money, and your files might not be even worth that much. So if that is the case, then get rid of this infection.
If your computer in unprotected, then it can become infected with Microsoft Decryptor Ransomware and it will encrypt all of your valuable files. Unfortunately, there is no method of decrypting them without paying the hefty ransom, so we recommend that you delete this ransomware either by using our manual removal guide or SpyHunter, our recommended antimalware application.
How to remove this infection
- Simultaneously press Windows+E keys.
- enter %TEMP% in the File Explorer’s address box.
- Identify the randomly named CLSID folder (e.g. {C3F31E62-344D-4056-BF01-BF77B94E0254})
- Identify the malicious .dll file (e.g. api-ms-win-system-softpub-l1-1-0.dll)
- Right-click the file and click the Delete button.
- Then, go to the locations below and delete the randomly named files.
- %USERPROFILE%\Desktop\[random name].bmp
- %USERPROFILE%\Desktop\[random name].html
- %USERPROFILE%\Desktop\[random name].txt
- %ALLUSERSPROFILE%\[random name].bmp
- %ALLUSERSPROFILE%\[random name].html
- Empty the Recycle Bin.
In non-techie terms:
Microsoft Decryptor Ransomware is a unique infection to due to its file structure and distribution method, so if your computer is not protected by an anti-malware program, then this malware can easily infect it. If your computer is infected with this ransomware, then it will encrypt all of your valuable files and demand an outrageous amount of money if you fail to meet the payment deadline.
