Even though ransomware infections are no longer as prevalent as they used to be some time ago, researchers working at Cisco Talos still monitor them every day to be able to identify large ransomware campaigns. Despite the fact that ransomware infections are primarily distributed via malicious spam emails, four brand new ransomware campaigns have been spotted recently. They are all directly associated with GandCrab, a nasty widely-distributed ransomware infection that has been designed by cyber criminals seeking to obtain money from users. Like many other ransomware infections, it is, traditionally, spread via spam campaigns and various exploit kits, including Rig and Grandsoft; however, there is serious evidence that compromised websites are used to deliver GandCrab too. This clearly shows that the recent decline in the prevalence of ransomware infections means nothing – cyber criminals might start distributing these infections actively again using new distribution methods at any time. That is, it is only a question of time when they will strike again.
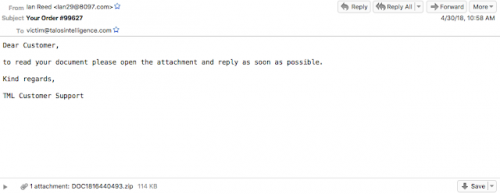
A number of compromised websites used to deliver GandCrab Ransomware were found during the research carried out by specialists at Cisco. Let’s start from the beginning. Specialists at Cisco Talos observed a spam campaign masqueraded as an ordinary online order on April 30, 2018 for the first time. The subject line of such an email was Your Order #{Random Digits}, for example, Your Order #995621. The email itself contained a short message: “Dear Customer, to read your document please open the attachment and reply as soon as possible. Kind regards, TML Customer Support.” Also, the spam email contained an attached .zip file holding a Word document. Opening this document is where all the problems begin because it contains a macro that automatically downloads and executes GandCrab Ransomware from the compromised website. As was observed during the course of the analysis, not all emails were the same. For example, others contained VBScript files instead of .zip archives. Without a doubt, the end result is the same – GandCrab Ransomware is dropped on the user’s computer when the Word document is opened. Interestingly, the latter campaign leveraged certutil.exe, installed as part of Certificate Services, which is quite unique.
On May 2, 2018, Cisco observed another wave of spam emails. It did not differ much from the initial campaign, but there was still one noticeable difference – the location of the payload. The payload was being hosted on hxxp://172.104.40[.]92/js/kukul.exe. Even though there was nothing special about it at first glance, an in-depth analysis showed that it was, actually, a legitimate but compromised website (www[.]pushpakcourier[.]net). It belongs to the courier company located in India. As for the third campaign, the similar spam email was used, but, again, the location of the malicious payload was a compromised legitimate WordPress-based website Herbal Treatment Advisory (hxxp://herbal-treatment-advisory[.]com). On May 5 and 7, 2018, one more campaign using the same template was observed by specialists. In this case, legitimate websites used some days ago were leveraged again for malicious purposes. This clearly shows that it is not so easy for small companies to keep their websites clean. So what was the reason these websites were compromised? The biggest problem is outdated software. Not all companies manage to update software in time. Others simply lack time and expertise to do this, so, without a doubt, more attention should be paid to this problem.
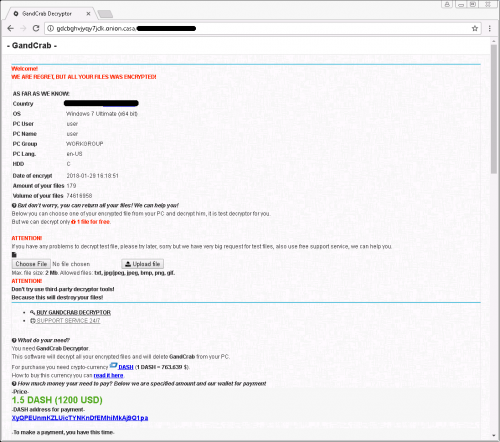
As mentioned previously, the distributed infection GandCrab Ransomware is a harmful malicious application that has been developed and is mainly used by cyber criminals for money extortion. Once it infiltrates computers, it soon locks files found on the affected system using the AES (Advanced Encryption Standard) algorithm. It targets pictures, documents, videos, music, and many other files. After encrypting all these files, it marks them with the .GDCB or .CRAB extension (it depends on the version of the ransomware infection). Then, a ransom note with payment instructions is dropped. Originally, GandCrab Ransomware demands a ransom in Dash, which is another cryptocurrency similar to Bitcoin. The size of the ransom might vary, but it usually demands 1.5 Dash. It should be noted that GandCrab Ransomware is extremely prevalent in South Korea, China, Russia, and the USA, but, of course, it might illegally infiltrate computers despite the user’s location.
It is not very likely that cyber criminals behind GandCrab Ransomware will stop scanning the web looking for new websites that could be used for the distribution of this malicious application anytime soon, so website administrators should not forget to regularly check for new available patches and updates and install them. Talking about ordinary computer users, they should stay away from all spam emails, especially those with the Your Order #{Random Digits} subject line. It would also be smart to keep security software enabled on the system.
References:
Biasini, N., Lister, N., and C. Marczewski. Gandcrab Ransomware Walks Its Way onto Compromised Sites. Cisco Talos blog.