Do you know what Krypton Ransomware is?
Have you become a victim of the vicious Krypton Ransomware? If you have, the chances are that you opened a corrupted spam email attachment representing the launcher of this infection. This scam is very successful, and most ransomware creators use it for the purposes of malware distribution. Once the infection is in, it silently encrypts files, and it is meant to encrypt those with .txt, .doc, .html .jpeg, .pdf, and similar extensions. The threat purposefully encrypts personal files that you have created yourself because these are the files you cannot replace; unless, of course, you have backups. Do you back up your files regularly? If you do, you should not postpone the removal of Krypton Ransomware for any longer. Once the threat is eliminated, delete the corrupted files, and then connect to your backup to retrieve personal files. If you do not have backups, the recovery of files might be impossible, but you still need to eliminate the malicious ransomware.
Krypton Ransomware has something in common with KoreanLocker Ransomware, Satan’s Doom Ransomware, Genocheats Ransomware, and hundreds of other threats alike. They all were created using the same Hidden Tear open source code. Our research team has analyzed most of these threats, and, in many cases, they are not completed or they do not function properly. That is because amateurs can use the source code to build malware. That being said, although Krypton Ransomware does not appear to be completed, this could change in the future, and so we cannot guarantee that you will not become a victim of this malware. When the encryption starts, this infection adds “.kryptonite” to the original names of the corrupted files, which can make it easier for you to check which ones were corrupted. Afterward, the malicious Krypton Ransomware might change the Desktop wallpaper using a file named “krypton.png,” and the text on this image file informs that a ransom of $150 must be paid within one week to ensure the decryption of files. There is one more TXT file. It is called “KRYPTON_RANSOMWARE.txt,” and you should find it in the test.Krypton folder on the Desktop. This file also encourages the payment of the ransom. We recommend deleting these files right away.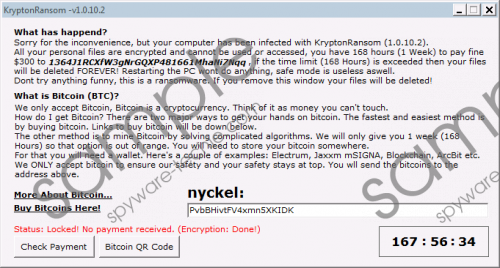 Krypton Ransomware screenshot
Krypton Ransomware screenshot
Scroll down for full removal instructions
The TXT files are not the only ones that are used by Krypton Ransomware to deliver the ransom demands. The infection also launches a window with full instructions that include the Bitcoin Address to which the ransom must be paid. The strange thing is that according to this message, the ransom is $300, which, of course, is much higher than the initial sum represented via the “krypton.png” file. If you are thinking about paying the ransom, think again, and do it carefully. The creator of the malicious Krypton Ransomware wants you to believe that you can recover your files only if you do as told, but our experience shows that you are unlikely to be given a decryptor, and so by getting involved in the payment of the ransomware you only guarantee the loss of your savings.
When Krypton Ransomware slithers in, it immediately creates a startup file, “krypran.exe.” You can find it in the %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\ directory. Because of this file, the infection will start running immediately when you start your operating system. The infection also ensures that the Task Manager is killed every time the user opens it, and that makes it impossible to delete Krypton Ransomware manually in normal mode. The good news is that you can reboot to Safe Mode to eliminate this threat. If you are not ready to remove the ransomware manually, reboot to Safe Mode with Networking and install a legitimate, automated anti-malware program. You might be able to successfully download and install this program in normal mode too.
Remove Krypton Ransomware
- Reboot your operating system to Safe Mode.
- Launch Task Manager by tapping keys Ctrl+Shift+Esc.
- Click the Processes tab, identify the malicious process, and right-click it.
- Select Open File Location and then End process in the Task Manager.
- Delete the .exe file that was linked to the process.
- Launch Explorer by tapping keys Win+E.
- Enter %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\ into the bar at the top.
- Delete the file named krypran.exe.
- Delete malicious ransomware-related files in these directories:
- %USERPROFILE%\Desktop
- %USERPROFILE%\Downloads
- %TEMP%
- Empty Recycle Bin to eliminate the deleted components.
- Install a legitimate malware scanner and then perform a full system scan.
How to reboot to Safe Mode
Windows 10 or Windows 8
- Tap Ctrl+Alt+Delete keys to open a menu.
- Click the Shut down options menu, which is next to the Power button.
- Tap and hold the Shift key on the keyboard and then click Restart.
- Open the Troubleshoot menu and then click Advanced options.
- Navigate to Startup Settings and then click Restart.
- In the boot options menu select Safe Mode (F4) or Safe Mode with Networking (F5).
Windows 7, Windows Vista, or Windows XP
- Restart the computer and wait for the moment BIOS loads.
- Immediately start tapping the F8 key to access the boot options menu.
- Select Safe Mode or Safe Mode with Networking using arrow keys and then tap Enter.
In non-techie terms:
Krypton Ransomware is a threat, and if you let it into your operating system – which, of course, you would do without realizing it – it will encrypt your personal files. Once files are encrypted, there is nothing you can do to save them. The developer of the ransomware delivers a message informing you that you can recover your files if you pay a ransom of $150/$300, but we can assure you that you would not get anything in return of this payment. In the best case, you have backups, and you do not care about the corrupted copies. If backups do not exist, make sure you start backing files up once the devious ransomware is removed from your system. To delete Krypton Ransomware, you need to reboot to Safe Mode or Safe Mode with Networking first because the infection is capable of messing with the Task Manager. We strongly recommend installing an anti-malware tool to have infections eliminated automatically, but if you want to delete the ransomware yourself, follow the guide above.
