Do you know what Korean Ransomware is?
Korean Ransomware comes from the exotic South Korea to encrypt your files and offer you to purchase the decryption key for an unspecified sum of money. You can try paying the ransom, but it does not necessarily mean that you will get your files back because the cyber criminals might not hold their end of the bargain. Therefore, we recommend that you remove it from your computer as soon as possible. Alas, to date, no free decryption tool can decrypt your files, so you can either wait for it to be released, if it ever will, or recover as much of your files as possible from external storage drives.
Our researchers have tested this ransomware’s sample and discovered that it does not encrypt anything. However, this may soon change since it looks as if it is still a work in progress. As you can already tell from its name, Korean Ransomware comes from South Korea and most of its text is the Korean language, but this does not mean that the ransomware is restricted to the country of South Korea. We have yet to discover how it is distributed, but we think that we will soon find it dropped by Trojans found in fake emails. Our researchers say that this ransomware is based on the hidden-tear project that has since been abandoned. Hidden-tear was an open-source ransomware project that has spawned up to 24 ransomware variants, and Korean Ransomware is one of them.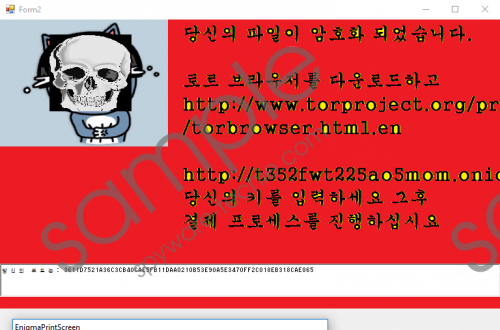 Korean Ransomware screenshot
Korean Ransomware screenshot
Scroll down for full removal instructions
The purpose of ransomware is to encrypt the files on the victims' computer's and demand that they pay a ransom for the decryption tool/key. As of yet, this particular ransomware is unable to encrypt any files, but researchers say that this is temporary. Still, we know that its encryption is based on the AES-256 encryption algorithm which is an industry standard for ransomware-type infections. Still, this encryption method is quite strong and will render your files useless once they have been encrypted. Our security experts say that it is configured to encrypt .txt, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .odt .jpg, .png, .csv, .sql, .mdb, .hwp, .pdf, .php, .asp, .aspx, .html, .xml, and .psd file formats. Take note that this ransomware targets files that are more likely to feature valuable information, such as work-related documents, valuable pictures and images, and so on.
Now let us discuss the encryption process in greater detail. Our researchers say that it appends the files with the .암호화됨file extension which means “encrypted” in Korean. Furthermore, it drops a file named ReadMe.txt. This file contains text that reads “당신의 파일이 암호화 되었습니다.G2BGZjucG=SCUfL” The English translation of the part in Korean means “Your files have been encrypted. G2BGZjucG=SCUfL” Also, Korean Ransomware will change the desktop wallpaper with text on a red background that also reads “Your files have been encrypted.” This image is the ransom note, and it also says that you have to download the TOR browser and enter your ID code supplied in the ReadMe.txt file. The random note also features a website address in which you have to enter the ID code. This site looks very similar to that of CrypMIC ransomware and Microsoft Decryptor Ransomware.
If your files have been encrypted by Korean Ransomware, then you can either pay the ransom and hope for the best or refuse to pay and remove it. Researchers say that you have to delete its main executable that should have a Kakao Talk icon. Researchers say that the main executable can be named KakaoTalk.exe or Korean-HT.exe. Consult the manual removal instructions below or download SpyHunter to eradicate this ransomware automatically.
Removal Instructions
- Find KakaoTalk.exe or Korean-HT.exe (name can vary)
- Right-click it and Click Delete.
- Empty the Recycle Bin
In non-techie terms:
Korean Ransomware is no different from the hundreds of other ransomware-type infections. It is configured to encrypt your files and offer you to buy the decryption key needed to decrypt them. However, you should not pay the ransom because you might get the promised decryption key. Therefore, we think that the only logical solution to this problem is to delete this infection and try to recover your files via Shadow Volume Copies or use backups if you have them.
