Do you know what KillerLocker Ransomware is?
KillerLocker Ransomware is a Portuguese malware threat that seems to be unfinished yet. There is a chance that the authors will finish this malicious program in the near future and it will become “deadly” as its name suggests; however, since it has been discovered by researchers, including our team, it may also become an abandoned project. If this was a fully finished program, it could strike a major blow to your computer as it can encrypt all your most important files, including executables. The only chance to recover your files after such a dangerous attack would be to risk paying the demanded ransom fee or use a recent backup you probably saved on a removable drive. But since this ransomware is not a fully-working one and we have not yet found it spreading on the web, you can actually decrypt your files and remove KillerLocker Ransomware from your system.
Although our researchers have not found this ransomware being distributed massively, we can still assume how it will be spread once it reaches the finished status; if at all. We consider it essential for you to know how such a threat can infiltrate your system in order for you to be more prepared and able to avoid the next attack. The mostly used method is most probably spamming campaigns. This means that you may get a spam e-mail that looks totally legitimate and refers to an unpaid invoice, an issue with wrong credit card details, an undelivered parcel, and so on. This mail will have a file attachment that can show up as an image or text file; although, in reality, it is a malicious executable file, most often a Trojan infection.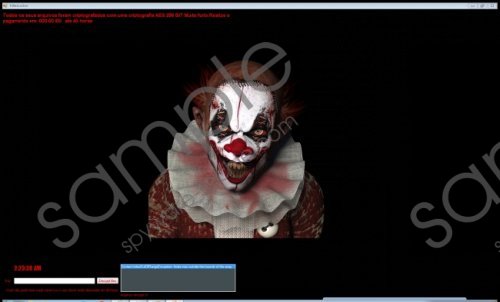 KillerLocker Ransomware screenshot
KillerLocker Ransomware screenshot
Scroll down for full removal instructions
The trick is to convince you that you must see this attachment because the moment you save it onto your hard drive and run it to see the content, you actually infect your system with this ransomware. This is why it is so important that you understand that even if you have a spam filter, such spam mails might end up in your inbox or other folders. You need to become more cautious about which mails you open to be able to protect your computer.
Another method that could be used is called Exploit Kits. This simply means that cyber criminals can take advantage of your browsers and drivers (Java and Flash) when these are not updated regularly. Older bugs could be used to drop infections like KillerLocker Ransomware onto your computer. We recommend that you keep all your programs and drivers up-to-date all the time to avoid such malicious attacks. Because if a working version of this ransomware lands on your system, it will be too late to realize its presence and act upon it by deleting KillerLocker Ransomware because all your files will have been encrypted by then.
Most unfinished ransomware programs we have seen lately do not even get to the point of encrypting your files. This infection however actually does what it claims. It uses the well-known AES-256 encryption algorithm to encrypt every file in your %ProgramFiles%, %APPDATA%, %USERPROFILE%\Desktop, %USERPROFILE%\MyPictures, and %LOCALAPPDATA% directories. The encrypted files get a ".rip" extension and become unusable until decrypted. After finishing with your files, this infection drops a text file on your desktop called "key.txt" that contains the hardcoded decryption key, which was "chavekey12345678910" in our case.
The whole encryption may not take more than half a minute, which does not give you enough time from launch till accomplishment to react to this damage. As a matter of fact, in this particular case, it would be a big mistake to delete KillerLocker Ransomware and soon you will understand why. The ransom note window comes up on top of all your active windows but this one you can easily close or change with the Alt+Tab combination. You can see a weird clown in the middle of this window, which is rather scary. All you learn from this note though that your files have been encrypted with the AES-256 algorithm and you have 48 hours to pay the ransom fee; and all this in Portuguese. This means that this ransomware will most likely target Portuguese users once it is finished. However, there is no information about the amount of money you should transfer, no Bitcoin wallet address given, and neither are you given a contact e-mail or website. Instead, you can simply enter the decryption code into the field called “Key” and press the “Decrypt files” button to recover all your files. This is why it is not worth closing this window or removing this ransomware. Once you manage to recover your files, you can simply remove KillerLocker Ransomware from your computer without further ado.
If you are ready to act, please follow our instructions below that contain all the necessary steps to delete this unfinished version of KillerLocker Ransomware. It is really not too complicated, so even if you are not an experienced user, you can simply do it. Nonetheless, it should be clear by now that if you want to keep malicious programs away from your system, you need to become a more cautious computer user and web surfer. If you are looking for an automated solution, we suggest that you use a malware removal application that can automatically safeguard your computer from all possible malware threats.
Remove KillerLocker Ransomware from Windows
- Open the “key.txt” file on your desktop.
- Copy the decryption password and paste it in the field provided at the bottom of the ransom note screen.
- Press the Decrypt files button.
- After the decryption is done, close the ransom note window.
- Press Win+E to launch File Explorer.
- Locate the downloaded malicious file and delete it.
- Bin the “key.txt” file from your desktop.
- Empty your Recycle Bin.
- Restart your PC.
In non-techie terms:
KillerLocker Ransomware is an unfinished malicious program that has not hit the web yet, but it has the potential to become your next nightmare. The version our researchers tested in our internal lab actually drops a text file on the desktop that contains the hardcoded decryption password. This version encrypts your most important files targeting certain directories and then displays its ransom note with a scary clown image right in the middle of this window. However, there is no information about the demanded ransom fee or any ways to contact these criminals to transfer the fee for the decryption key. Instead, you can simply paste the key you find in the text file and decrypt the files yourself before you set out to remove KillerLocker Ransomware from your system. If you want to keep your computer safe from similar but more dangerous attacks, you should install a reliable anti-malware application that will automatically take care of all your security issues.
