Do you know what Jhon Woddy Ransomware is?
Ransomware might quickly become a user’s worst nightmare because these infections target users’ personal files. Jhon Woddy Ransomware is one of the newest members in the category of ransomware infections. Despite the fact that it is a new product of cyber criminals, it does not differ much from older threats which also seek to make users pay money. Crooks are not dumb – they know that it is hard to lure users into paying money. As a consequence, ransomware infections are programmed in such a way that they could encrypt the personal data stored on the computer. This data consists of documents, pictures, videos, and even important programs. Jhon Woddy Ransomware encrypts all those files too once it successfully enters computers, but, luckily, it does not seek to ruin the Windows OS running on the computer, so it does not touch system files. We understand that you badly need to get your files back, but we are still strictly against making payments to cyber criminals because the key they claim to have is quite expensive and there are no guarantees that it will be ever sent to you. Find alternative file decryption methods presented further in this article – you might be able to recover files without the special decryption tool!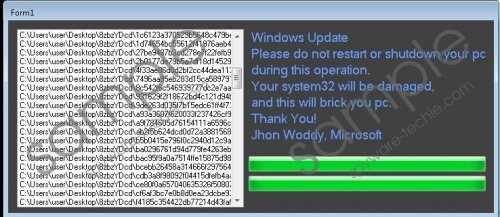 Jhon Woddy Ransomware screenshot
Jhon Woddy Ransomware screenshot
Scroll down for full removal instructions
There is no doubt that Jhon Woddy Ransomware has successfully entered the computer if all files have received a new filename extension .FUCKED and their names have been changed. Also, you should see a window containing a ransom note. Actually, the ransom note is not opened for users the second Jhon Woddy Ransomware is inside the computer. Instead, users see a fake Windows Update window first:
Windows Update
Please do not restart or shutdown your pc during this operation.
Your system32 will be damaged, and this will brick you pc.
Thank You!
Jhon Woddy, Microsoft
The fake window is displayed for users to make sure that they do not restart or shut down their computers and terminate the file encryption process. Since the window contains the magical word “Microsoft”, people act exactly how they are told, i.e. they do not turn off or restart their PCs, allowing ransomware to finish what it has started. When it finishes its job, a small window “Form2” is opened. It informs users that all their files have been encrypted and now they have to send 0.3 Bitcoin to the Bitcoin address provided in the ransom note within 72 hours. Users are told there that all files will be automatically decrypted when the required amount of money in Bitcoins is transferred. There are many cases when users get nothing even though they send money to crooks, so our team of experienced specialists does not think that it is a good idea to pay money. What users can do to get files back without the special decryptor cyber criminals have is to recover files from a backup. If you have never backed up your important files, you should use third-party data recovery software – we do not promise that it will allow you to recover all files, but it is definitely worth a shot.
The successful entrance of a ransomware infection shows that the computer is unprotected. As our team of specialists has managed to find out, the majority of ransomware infections are spread through spam emails, so, most probably, you have Jhon Woddy Ransomware inside your computer because you have opened an attachment from a spam email too. Do not do that ever again if you do not wish to find your files encrypted by another ransomware infection. Since ransomware infections are sneaky threats that do not need permission to enter computers, security specialists recommend installing a reputable security tool. It will not allow any new computer infection to sneak onto your PC.
Jhon Woddy Ransomware does not create any files on the infected computer, so it will be gone after the removal of the malicious file. Before you do that, kill the malicious process belonging to this ransomware infection so that you could access your PC and find this file. If you cannot find the malicious file, kill the malicious process and then download an automatic malware remover, e.g. SpyHunter. It will clean the system in no time.
Delete Jhon Woddy Ransomware
- Press Ctrl+Shift+Esc.
- Click Processes to open this tab.
- Right-click on the malicious process and select End Process.
- Go to find the malicious file of the ransomware infection (it might be located in %APPDATA%, %TEMP%, %USERPROFILE\Downloads, or %USERPROFILE%\Desktop).
- Delete it.
In non-techie terms:
If Jhon Woddy Ransomware has sneaked onto your computer so easily, there is a possibility that other computer infections are actively working on your computer too. Scan your PC with an automatic scanner after the manual Jhon Woddy Ransomware deletion to find out whether or not it is true. You do not need to perform the system scan with an automatic malware remover again if the ransomware infection has been erased automatically – all other threats have been taken care of too.
