Do you know what Jack.Pot Ransomware is?
Jack.Pot Ransomware is a nasty infection that, as has been found by analyzing its code, was released on the 14th of March, 2016. Even though it is almost 9 months old, it is evident that it is not very popular yet. According to specialists, it is still in development mode, so cyber criminals do not distribute it actively yet. Of course, it does not mean that it is impossible to encounter it. The first symptom showing that Jack.Pot Ransomware is inside your computer is the inability to access files located in %USERPROFILE% and its subfolders. All these files which you cannot open should have a new filename extension .code so that it would be possible to say that Jack.Pot Ransomware is surely on the system. Users suspecting that a ransomware infection has sneaked onto their computers should read this article for more information. Unfortunately, at the time of writing, it is hard to say whether or not it would be possible to unlock files because this computer infection is quite new, and it has not affected many users yet. Even though there is not much information about the decryption of files, you have to remove this ransomware infection as soon as possible. If you do not do that, it will keep running and looking for new files to encrypt on your computer. Yes, unlike other similar threats, Jack.Pot Ransomware does not delete or terminate itself after the encryption of personal files it finds on the infected computer.
There is one more symptom indicating the successful entrance of Jack.Pot Ransomware. Users make complaints that they see a window with a message covering the entire Desktop, and they cannot close it. This message in full-screen is a ransom note left by this ransomware infection. It informs users about the encryption of files by saying “All your important files are encrypted.” Just like other ransomware infections, it also tells users that they have to pay 3 BTC (at the time of writing, 3 BTC equals 2188 USD) if they wish to have their files decrypted. You should not even try to transfer the required money, according to our team of experts. It is because the provided Bitcoin address does not exist. In other words, your money will not reach cyber criminals, and, consequently, nobody will unlock files for you. Unfortunately, users cannot do much to decrypt their files. The only way to get them all back is to recover them from a backup you have created before the entrance of this malicious application. If you do not have a backup of files, your only hope is a free decryption tool which might be developed in the future by specialists (if it turns out that files can be decrypted).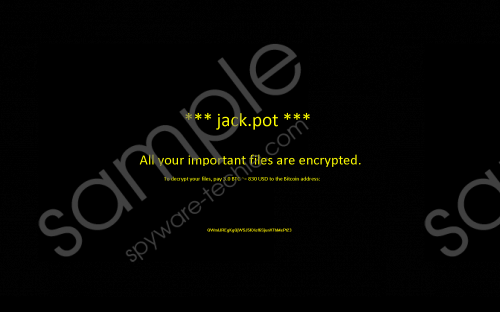 Jack.Pot Ransomware screenshot
Jack.Pot Ransomware screenshot
Scroll down for full removal instructions
Users have to delete Jack.Pot Ransomware as soon as possible from their systems because it will not only keep searching for new files to encrypt, but will also keep communicating with an IP address 52.58.55.93 (C&C server). In other words, it will use your Internet connection without permission, and it might even get updates from there in the future. Finally, you could not access your Desktop and thus use your computer normally because the screen-locking window cannot be removed once and for all without the full removal of Jack.Pot Ransomware.
What you need to do to terminate Jack.Pot Ransomware is to press Alt+TAB to close the black window and then kill the process of this malicious application in the Task Manager. On top of that, the malicious file belonging to the ransomware infection has to be found and deleted. It should be located in the Downloads folder; however, if you cannot find it there, you should use an automatic malware remover (e.g. SpyHunter).
Delete Jack.Pot Ransomware
- Tap Alt+TAB simultaneously to close the black window.
- Tap Ctrl+Shift+Esc.
- Open the Processes tab.
- Right-click on the process of the ransomware infection.
- Click End Process.
- Close the Task Manager.
- Find and erase the malicious file you have launched (it should be located in the Downloads folder).
- Scan your PC with SpyHunter.
In non-techie terms:
Users might quickly encounter another ransomware infection if they do not do anything to protect their computers. It has been revealed that such threats usually enter computers when users open spam emails and download attachments they find in them; however, it is definitely not the only way malware is distributed. Therefore, all users surfing the web on a daily basis should install security software. Keep in mind that only reputable scanners work well and can help you to protect your PC from computer infections.
