Exploit kits, throughout the years, have been successfully used for the deployment of all kinds of malicious infections. In the most recent years, during the rise of file-encrypting ransomware, they were often employed for the distribution of some of the most infamous threats, including Cerber Ransomware and Spora Ransomware. Exploit kits, however, are not untouchable. In 2016, two highly active exploit kits, Angler and Nuclear, disappeared due to reasons that are unknown to this date. Last year, we saw the dissolution of the Sundown EK after its source code was leaked online, and another well-known exploit kit, Neutrino, appears to have been abandoned too. Now might be the time for the infamous RigEK. Although this exploit kit is still functional, it was recently discovered that its usage has decreased by 92%. Also, it was found that the kit is no longer predominantly used for the distribution of ransomware.
Malware researchers at Palo Alto Networks have recently published an analysis showing how the use of RigEK has decreased within the last year. They analyzed this by searching “AutoFocus for items tagged RigEKFlashContainer seen through web traffic over port 80.” The analysis showed that while there were 812 verified sessions in January of 2017, only 65 sessions with hits on “RigEKFlashContainer” were recorded in January of 2018. This shows a 92% decline. There are several reasons for this. First of all, the pseudo-Darkleech campaign, which was responsible for Cerber Ransomware, seized its activity. This alone accounted for a 50% drop. Soon after this, another campaign, EITest, changed its course of action too. Before that, it was focusing on the deployment of CrytoMix Ransomware, CryptoShield Ransomware, and Spora Ransomware. In 2017, however, the actors behind the campaign switched to different techniques. This caused a drop of another 50% for the RigEK.
Exploit kits became less effective once four new updates were applied to Google Chrome, which made it stronger against exploit kits that use vulnerabilities to deploy malware. It is easiest for attackers to exploit Internet Explorer and Microsoft Edge browsers, and since the use of these browsers has been declining, the effectiveness of exploit kits has been declining as well. While ransomware is still posing a major threat, it has been observed that cyber attackers have moved on from file-encrypting and ransom-demanding threats to cryptocurrency miners, which silently use systems’ resources to make money. While the activity of crypto miners can be disruptive because the systems can be drained of power, which could lead to dramatically decreased performance levels or even computer crashes, they do not pose virtual security risks to victims. Of course, no one wants a crypto miner on their operating system, and we cannot stop analyzing and tracking exploit kits that spread them.
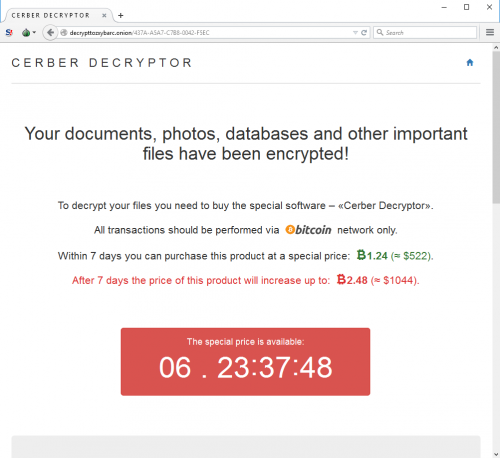
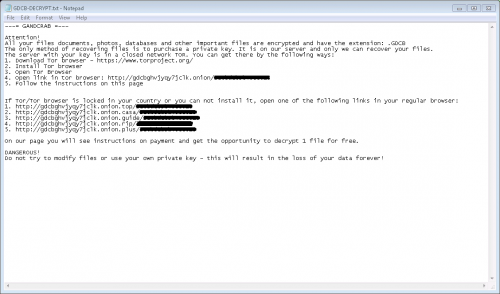
Although RigEK operates on a much lower scale, it is still active, and it is still used for the deployment of various malware, not just coin miners. There are three specific campaigns that we need to track very carefully. One of them is known as “Seamless,” and it was found to be spreading the Ramnit Trojan, which is a known information stealer. Another campaign, “Fobos,” is spreading the Bunitu proxy Trojan. We cannot forget about “Ngay,” which, alongside the Remcos Trojan, also distributes coin miners. Palo Alto Networks researchers report that 65,512 samples of coin miners were linked to RigEK in January 2018, which is a significant number compared to the 2,368 samples detected in January 2017. That being said, while coin miners appear to be the main cash cow behind the Rig Exploit Kit, ransomware is still spread using it. Just recently, the malicious GandCrab Ransomware started spreading with the help of this infamous exploit kit. The malware can spread when the exploit kit uses a vulnerability in Internet Explorer and Flash Player.
Does the Rig Exploit Kit predict the end of ransomware? That is unlikely to be the case; at least, not just yet. Nonetheless, it is possible that ransomware is no longer as lucrative as it used to be in the past, and while major players are targeting big companies and governments, cyber criminals who are operating on a lower scare and who are simply using any chance to earn a dirty penny might be looking for new opportunities. At the moment, cryptocurrency miners are able to satisfy the need. Overall, the reasons behind the RigEK’s decline are pretty clear, and all we can really do right now is observe the situation and look out for any new exploit kits that might emerge in the near future and replace RigEK.
References
Duncan, B. February 26, 2018. Rig EK One Year Later: From Ransomware to Coin Miners and Information Stealers. Palo Alto Networks.
Duncan, B. June 21, 2017. Decline in Rig Exploit Kit. Palo Alto Networks.
Palmer, D. January 31, 2018. Ransomware crooks test a new way to spread their malware. ZDNet.
Digital Shadows Analyst Team. August 16, 2017. Fluctuation in the Exploit Kit Market – Temporary Blip or Long-Term Trend? Digital Shadows.