Do you know what TeslaCrypt ransomware is?
TeslaCrypt ransomware has several different versions. The newest ones are those which attach the .CCC or .VVV filename extensions. In most cases, all the versions of this infection enter systems unnoticed and immediately start performing their main activities. It is known that the main aim of ransomware infections is to extort money from innocent computer users, so TeslaCrypt ransomware will also do everything what it takes in order to achieve this aim.
Once TeslaCrypt slithers onto computers and performs its major activities, it adds the .VVV filename extension to each of the files. The “filename extension” is often described as a suffix that is placed next to the name of the file. It is separated by a dot. Users who get infected with TeslaCrypt usually notice such files as video.mp4.vvv, myphoto.jpg.vvv, and documents.docx.vvv. The presence of the .VVV filename extension simply shows that these files are encrypted. In other words, they are locked using a very strong key that is known to be RSA-2048. As TeslaCrypt ransomware will add .VVV to every encrypted file, it is not difficult to understand that it basically encrypts all of them. Researchers have observed that this threat is primarily targeted at files that belong to games, but it can encrypt you photos, videos, documents, and other files too. Generally speaking, TeslaCrypt will touch hundreds of files with the following extensions: .pptx, .xlsb, .xlsm, .docm, .docx, .d3dbsp, .ibank, .pkpass, .icxs, .hplg, .mdbackup, .syncdb, .mcgame, .layout, .blob, .dazip, and others.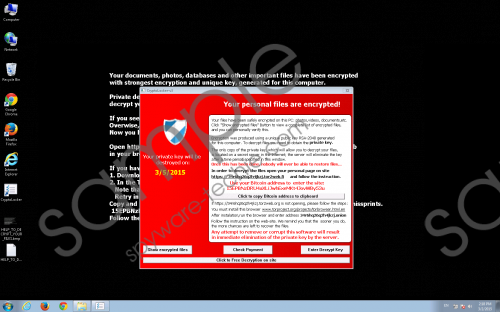 How to Remove VVV File Extension screenshot
How to Remove VVV File Extension screenshot
Scroll down for full removal instructions
There are three main versions of TeslaCrypt ransomware. Different versions add different filename extensions to files after they encrypt them. For example, the version that adds the .ECC filename extensions is considered to be the oldest one, whereas those that attach .CCC and .VVV extensions are considered to be the newest. The new version of this ransomware will also change the TOR, which is used to pay a ransom, payment site gateway. Last but not least, the format of the files with instructions might be changed too. Users will see how_recover+abc.html or howto_recover_file_*.txt additional files on their desktop and in some folders.
A number of tests have shown that this infection will not only encrypt all files and modify the registry in order to add .VVV filename extensions. Research shows that it is also capable of killing cmd.exe, msconfig, taskmgr, and other important system utilities temporary. After some time, it does not monitor whether they are launched anymore and users can open them. TeslaCrypt ransomware will also change wallpaper in order to convince users that their files have been really encrypted. The main instructions on how to pay a ransom in order to remove .VVV file extensions are also there. It has been observed that users have to make a payment in Bitcoins in order to gain access to files again.
Many specialists believe that you should not do that, especially if you have a backup of your major files or they are unimportant. Of course, if you need your files badly, you can pay a ransom, but there are no guarantees that the .VVV filename extension will be removed and you could open your files again. Yes, nobody can guarantee that you will be able to recover your files and, unfortunately, the free way to decrypt files does not exist for now.
It has been observed that this ransomware infection can come bundled with free applications. Actually, this is the main way how users end up with this ransomware. Furthermore, this threat can enter systems if users surf the web carelessly and visit web pages with an infectious content. TeslaCrypt ransomware might have entered the system together with software from torrent or file-sharing websites too. Finally, users might have initiated the entrance by opening an infectious email attachment too. TeslaCrypt is targeted at those PCs which have security loops, there are no security software installed, and the owners of such PCs surf the web in a careless way.
TeslaCrypt ransomware does not leave anything on the system after it adds the .VVV filename extension. It means that there is no need to remove it because it is already gone. Of course, the threat tends to come together with untrustworthy programs, which means that they might be present too. To check your PC, scan your system with the SpyHunter antimalware scanner. It will let you know the condition of your system within seconds, and it will remove the existing threats for you too.
In non-techie terms:
Ransomware infections are very popular threats these days. They enter computers with an intention of encrypting users’ files and obtaining money from them. A number of different file-encrypting threats are spreading through the web at the time of writing, so if nothing is done to ensure the maximum protection of the computer, a bunch of new files can become unusable due to the entrance of a new file-encrypting infection again.
