Do you know what Hades Locker Ransomware is?
Hades Locker Ransomware is a highly malicious application that was first discovered on the 6 October 2016. This newly released ransomware is very dangerous indeed because it is designed to encrypt your files and there is no way to decrypt them for free. Its developer wants to pay 1 BTC for the decryption tool and key, but they are too expensive and you might not get them once you have paid and we suggest that you remove it instead. So you might be better off just getting rid of this infection using the instructions provided. Still, we kindly invite you to read this whole description to find out more about this infection.
Unfortunately, at the time of this article, there is no information about this ransomware’s origins. Hence, we do not know how it is distributed, and the demographics that it targets are also unknown. For all we know, this ransomware is configured to be distributed around the globe. Its random note even gives us a shred of evidence by saying that 1 BTC is 600 USD, 500 EUR, and 400 GBP. Stating three currencies indicates that it is distributed in the US, UK, and EU at the very least. However, this is just speculation and more time will have to pass until more information about it comes to the surface.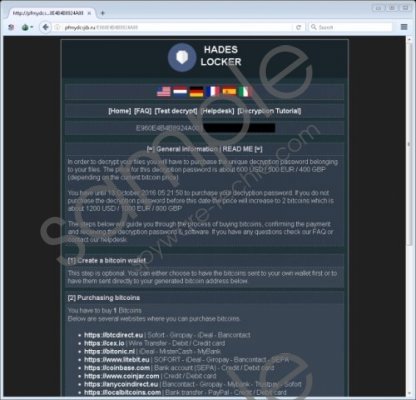 Hades Locker Ransomware screenshot
Hades Locker Ransomware screenshot
Scroll down for full removal instructions
Our malware analysts have acquired Hades Locker Ransomware’s sample and tested it on one of our test computers. Their analysis has shown that this ransomware that its executable is named randomly and is dropped in either %APPDATA%\wow6232node or %TEMP%\RarSFX0. Once on your computer it will run automatically and connect to a legitimate website at http://ip-api.com/xml. This site is designed to check the IP address, location, Internet Service Provider, and other information. This ransomware retrieves information from this website and send a unique ID called "hwid" to its main Control and Command (C&C) server. This ID contains your computer’s name, username, country, IP address. The C&C server then replies with a password to use to encrypt the files using the AES algorithm. During this process, this ransomware will store your unique ID and the status of the encryption process (be it 0 or 1) at the HKCU\Software\Wow6232Node registry key that has the values “hwid” and “status.” As you can see, there is a lot going on in the background while this ransomware preps for encrypting your files. Now let us move forward with its functionality.
Once the preparation phase is complete, this ransomware will begin encrypting files such on each mapped drive and content. Testing has shown that Hades Locker Ransomware can encrypt hundreds of file formats, so they include but are not limited to .3ds, .3g2, .3gp, .7z, .xlm, .xlr, .xlsm, .mp3, .mp4, .mpg, and .obj. Take note that it will append the files with a unique file extension that has “.~HL “ at the beginning followed by 5 more characters that are the first letters of the encryption password. Also, it will drop three different ransom notes named README_RECOVER_FILES_[victim_id].html, README_RECOVER_FILES_[victim_id].png, and README_RECOVER_FILES_[victim_id].txt in each folder where files were encrypted. However, according to our researchers, this ransomware will skip Windows, Program Files, Program Files (x86), System Volume Information, and $Recycle.Bin folders.
Once the encryption is complete, Hades Locker Ransomware will run the “WMIC.exe shadowcopy delete /nointeractive" command to delete all Shadow Volume Copies to prevent you from restoring some of your files. The ransom notes found in the folders of the encrypted and README_RECOVER_FILES_[victim_id].html in particular, says that you have one week to pay 1 BTC for the decryption tool and key and if you fail to meet the deadline, then the ransom will increase to 2 BTC. You can try paying the ransom, but there is no guarantee that you will get what you were promised.
In conclusion, Hades Locker Ransomware is one dangerous infection that can encrypt your files and to decrypt them will cost you a significant sum of money. Unfortunately, there is no free decryption method, but we suggest that you wait for it if your PC was infected with this ransomware. We also suggest that you remove it using SpyHunter or manually using the instructions provided below.
Removal Instructions
- Press Win+E keys.
- In the File Explorer’s address line, enter5 the following directories.
- %APPDATA%\wow6232node
- %TEMP%\RarSFX0
- Find the ransowmare’s executable.
- Right-click it and click Delete.
- The, go to one of the following addresses.
- %ALLUSERSPROFILE%\Start Menu\Programs\Startup (XP)
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup (Vista and over)
- Delete this ransomware’s point of execution (.exe file)
- Empty the Recycle Bin.
Delete the registry strings
- Press Win+R keys.
- Type regedit in the dialog box and hit Enter.
- In the Registry Editor, go to HKCU\Software\WOW6232Node
- Find “hwid” and “status”
- Right-click them and click Delete.
In non-techie terms:
Hades Ransomware Locker is designed to infect your computer in a clandestine manner and encrypt most of the files on it. It does this in order to extract money from you pay offering you to purchase a unique decryption key and decryption software to get them back. However, you should not comply with those demands because its developer might not give you the key. You can remove this ransomware using the guide presented above.
