Do you know what Gc47 Ransomware is?
If your operating system was infected by Gc47 Ransomware, you should receive a notification containing the email address “unixc47@gmail.com”. If this is the case, you might have already identified the threat that you are dealing with. This particular ransomware is not highly different from other threats of its kind, but it has unique traits, which is surprising, considering that it was built using the Hidden Tear open source code, which has been exploited many times before. When this threat invades your operating system, it immediately creates keys that are sent to the attacker and are also kept on your PC in specific files. Unfortunately, you are unlikely to have any use for these keys. If you are experienced, you might be able to build a decryptor and use these keys to free your personal files. Of course, few users are likely to have enough experience for that. Most will face the loss of their personal data. Continue reading to learn more about that and the removal of Gc47 Ransomware.
Enjey Crypter Ransomware, Redants Ransomware, and GhostCrypt Ransomware are few of many infections that were created using the Hidden Tear code. The distribution of these threats is unpredictable because their creators are the ones who handle that. Some might use spam emails, and others could attach the launcher to software bundles or conceal it as a fake installer. If you encounter the launcher of the threat, you are unlikely to realize it, and you might execute it without even suspecting a risk. Once the dangerous Gc47 Ransomware is executed, it immediately creates C.key and D.key files that are used for the encryption process. These files are most likely to be found in the “Documents” folder, and they are unique for every user. Right before the encryption begins, these files are silently sent to unixc47@gmail.com and then to admin@ransomware.com using the Simple Mail Transfer Protocol (SMTP). Gc47 Ransomware is also likely to introduce you to pop-ups with random messages right before the encryption starts. If you encounter such activity, you should consider the invasion of malware right away.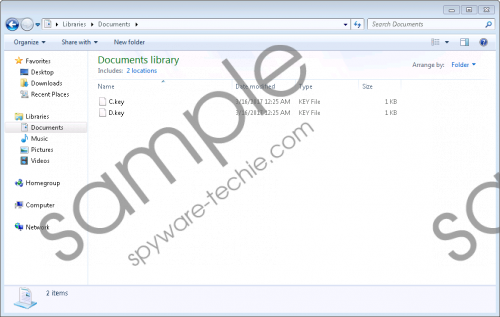 Gc47 Ransomware screenshot
Gc47 Ransomware screenshot
Scroll down for full removal instructions
As soon as Gc47 Ransomware encrypts your files and attaches the “.Fuck_You” extension to them, a TXT file is created, and it is meant to introduce you to very obscure instructions. According to them, you need to pay 50 USD to 14vY5z8fWzCj93YTwbGiLd6ansZNMJ2kC3 (Bitcoin Address) and email unixc47@gmail.com. There is no information suggesting what would happen if you acted accordingly, but it is most likely that the creator of the ransomware wants you to pay the ransom and initiate communication in return of a decryptor. Does it exist and will it be provided to you? These are two very important questions that, unfortunately, we do not have answers to. In general, paying the ransom is risky business, and you want to weigh all pros and cons because you want to be 100% sure about it before you make the payment.
When Gc47 Ransomware is executed, it should run a command “cmd.exe /C choice /C Y /N /D Y /T 1 & Del” to delete itself. If that is the case, you will not find the launcher. Of course, you do not know if the threat has erased itself from your PC or not, and so you have to do an inspection. Since it might be difficult to identify the malicious file, we strongly advise employing an anti-malware tool that can successfully find and erase all malicious components. If you choose to remove Gc47 Ransomware manually, make sure you keep C.key and D.key files because you might be able to use them in the future. If you employ an anti-malware tool, make sure to keep it updated so that all security vulnerabilities would be patched in time and malicious infections could not invade your operating system again.
Delete Gc47 Ransomware from Windows
- Launch Task Manager by tapping Ctrl+Shift+Esc.
- Move to the Processes tab and identify the malicious process.
- Select it and choose End task/End process.
- Find the launcher file of the malicious ransomware (check Downloads, Desktop, and Temp folders first).
- Right-click and Delete the file.
- Perform a full system scan so that no malicious leftovers would remain unnoticed.
In non-techie terms:
Gc47 Ransomware is one of the worst threats to invade your operating system because it can encrypt your personal files and demand a ransom in return of their decryption. Unfortunately, no one call tell if the files would be decrypted if you paid the requested 50 USD fee. At the moment, there is nothing else to do if your files were encrypted. Obviously, if you have backups, you do not need to worry about any of this. Although it might be very easy to remove Gc47 Ransomware manually, our research team suggests using anti-malware software for two simple reasons: It can get rid of all malicious threats automatically, and it can ensure that the protection of your operating system is at the highest level. If you have more questions, add them to the comments section below.
