Do you know what Executionerplus Ransomware is?
Executionerplus Ransomware is a very mysterious infection. Our research team, at the moment, is still collecting information and researching this threat, and if anything new is discovered, the information will be updated. For now, it appears that this file-encrypting ransomware is still in development. Of course, there is always a possibility that it was used as a test, and it will not be released as a real threat in the future. That being said, the current version of this threat appears to be built to encrypt files and demand a ransom from the victims. Read this report to learn more about the infection and ways to protect yourself against it. We also discuss the removal of Executionerplus Ransomware. Note that a comments section is available to you, and you can use it to ask questions or commence discussions.
File-encrypting ransomware infections are very common these days, and after researching the majority of them, we can say that they are usually spread using corrupted spam email attachments. This is the method of distribution that the creator of Executionerplus Ransomware might use as well. Of course, there are many different ways using which cyber criminals could spread this threat, and so it is not wise to focus on just one backdoor or vulnerability. The entrance of this infection is meant to be silent, and so you are unlikely to notice it. Once in, this threat deletes shadow volume copies – that is done using the “cmd.exe /c vssadmin delete shadows /all /quiet” command – to ensure that the victim cannot recover files manually. This command has been employed by many other infections, including Cobra Ransomware, Nuclear Ransomware, WininiCrypt Ransomware, and, of course, CryptoJoker Ransomware, whose code appears to have been used to create Executionerplus Ransomware. Needless to say, all of these threats require removal.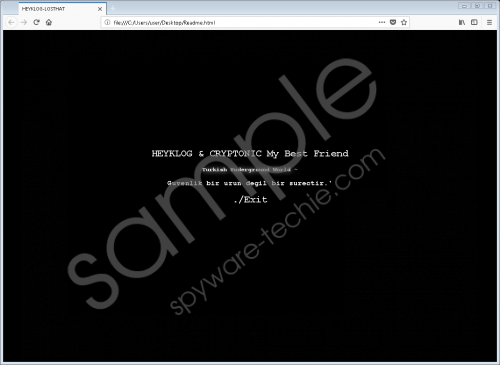 Executionerplus Ransomware screenshot
Executionerplus Ransomware screenshot
Scroll down for full removal instructions
If Executionerplus Ransomware ends up encrypting files, it should add the “.destroy.executioner” extension to the original names, but it was found that the “pluss.executioner” extension might be added to TXT files specifically. That is a unique trait. Another unique thing about this ransomware is found in the ransom note, which should be represented using the file named “Readme.html” (it should be created on the Desktop). According to our research, once the file is opened, a song named “Gucci Gang Remix” by Zero should be played from YouTube. This is the part that is most confusing as there are no real ransom demands. Maybe that is the thing that the creator of the ransomware is still perfecting. Overall, whether or not any demands are made, you should not pay attention to them. Instead, you should focus on deleting Executionerplus Ransomware and decrypting files if they were encrypted. It is reported that a decryptor might be offered by a user named “demonslay335” via Twitter.
At the time of research, Executionerplus Ransomware was not fully formed, which is why it is hard to discuss the removal of this threat. Most likely, the victims of this malware only need to delete the launcher file and the ransom note file to get rid of it completely. That being said, we cannot guarantee this, and if you choose to delete Executionerplus Ransomware manually, it is important to perform a full system scan to check if anything bad is still on your operating system. Obviously, if you find any malicious threats, you need to eliminate them immediately. Since manual removal can be complicated, we recommend utilizing anti-malware software. Not only will it erase all threats automatically but it will protect you in the future too.
Remove Executionerplus Ransomware
- Find and Delete any recently downloaded suspicious files.
- Delete the ransom note file named Readme.html on the Desktop.
- Empty Recycle Bin to eliminate malicious components completely.
- Install a trusted malware scanner and then perform a full system scan to check for any leftovers.
In non-techie terms:
If you have encountered the malicious Executionerplus Ransomware, the chances are that your personal files are now encrypted. It appears that it might be possible to decrypt files for free, and, hopefully, you can figure that out. Of course, whether or not you manage to decrypt files, you need to delete Executionerplus Ransomware, and it is best to do it using anti-malware software because besides erasing malware this software is also irreplaceable when it comes to protecting the system against other malware attacks in the future. If you choose to erase the infection manually, do not forget to employ a malware scanner afterward to thoroughly inspect your operating system for any leftovers.
