Do you know what Cyberresearcher Ransomware is?
Your files are very vulnerable if the malicious Cyberresearcher Ransomware manages to slither into your Windows operating system. This threat is capable of encrypting the data of images, documents, videos, and other personal files that might be stored on your computer. Unless you have copies of these files backed up externally, recovering them is unlikely to be possible, and you certainly should not follow the instructions that are introduced to you by the creator of the ransomware. If you do that, you are likely to lose a great deal of money, and we are sure that is something you want to avoid. Our research team has analyzed the threat, and the findings are presented in this report. Here, you can also find useful information on how to delete Cyberresearcher Ransomware. One thing to keep in mind is that the .exe file of the infection can be located anywhere, and so removing it manually can be challenging to most.
The suspicious Cyberresearcher Ransomware was created by an unknown malware developer, but it is possible that this was their first infection because it was built using the Hidden Tear open source code, which is available to anyone. It has been employed by the creators of Horros Ransomware, Sorry HT Ransomware, Scammerlocker Ransomware, and hundreds of other similar infections. Most often, they spread with the help of spam emails, and users usually execute the malware themselves by opening corrupted spam email attachments. If the infection is not removed in time, the encryption is initiated shortly, and once the files are encrypted, the “.CYBERRESEARCHER” extension is added to the names of the files to make it easier to identify them. Although Cyberresearcher Ransomware does not encrypt system files – which would be counterproductive – it can hit the most personal and valuable files because the victims are most likely to pay money to get those back. Unfortunately, paying the ransom is not really an option.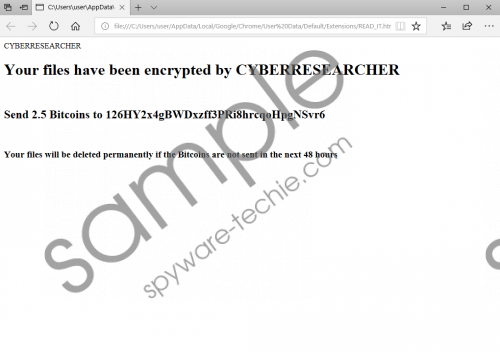 Cyberresearcher Ransomware screenshot
Cyberresearcher Ransomware screenshot
Scroll down for full removal instructions
The creator of the malicious Cyberresearcher Ransomware wants you to pay a ransom of 2.5 Bitcoin within 48 hours to get the files decrypted. This demand is introduced to victims via a ransom note file called “READ_IT.htm.” The infection communicates with a remote server to obtain this file, as well as the encryption key used for the corruption of your personal files. The developer of the infection has set up a special Bitcoin wallet, 126HY2x4gBWDxzff3PRi8hrcqoHpgNSvr6, to collect the ransom. At the time of research, no transactions had been sent to this wallet, and we are hopeful that the threat is not spreading actively. All in all, if it encrypts files successfully, users are pushed to pay a huge ransom, and doing that is not recommended because cyber criminals are unlikely to give anything in return.
As mentioned already, the executable of Cyberresearcher Ransomware can be located anywhere, and so if you cannot uncover this threat, you need to make sure you find another way to delete it. We suggest using anti-malware software because it automatically eliminates existing malware, and then, it continues protecting your operating system against other threats. If you are not interested in investing in software that would automatically remove Cyberresearcher Ransomware, you will need to erase the threats yourself, and the instructions below might be helpful in guiding you. A legitimate malware scanner can be very helpful as well when uncovering threats and tracking the removal processes.
Delete Cyberresearcher Ransomware
- Locate the launcher of the ransomware (might be placed on the Desktop, in the Downloads folder, or the %TEMP% directory).
- Once you find the file, right-click it and select Delete.
- Right-click and Delete the ransom note file, READ_IT.htm (note that copies might exist).
- Install a trustworthy malware scanner and perform a full system scan to check for malware leftovers.
In non-techie terms:
The malicious Cyberresearcher Ransomware might have invaded your operating system in a highly stealthy manner, but it does not hide itself once your personal files are encrypted. The threat adds a unique extension to the files it corrupts, and then it creates a file that presents a ransom note. This note suggests that the victim must pay a humongous ransom of 2.5 Bitcoins to a specified Bitcoin wallet within 48 hours to free the files, but cyber criminals can promise anything just to get the money, and, most likely, you would be wasting your money for nothing in return. Whether or not you get your files back – and you can recover them if they are backed up online or externally – you need to remove Cyberresearcher Ransomware. The instructions above provide a rough guide because the executable can be placed anywhere. If you are lost, install an automated anti-malware program to have the malicious file encryptor eliminated automatically.
