Do you know what CryptoKill Ransomware is?
CryptoKill Ransomware is a malicious application first detected in February 2017. It is based on the engine of an open-source ransomware Hidden-Tear, so it is not at all surprising that it also uses the AES encryption algorithm. Even though this infection has been categorized as ransomware by specialists, it slightly differs from malicious applications that receive the ransomware label. Unlike other ransomware infections, it does not demand money from users and does not even place a screen-locking window. Evidently, it does not try to obtain money at the time of writing. There is, of course, a small possibility that this will change soon because, at the time of writing, CryptoKill Ransomware is in a test version, judging from a folder it searches: %USERPROFILE%\Documents\test. Unfortunately, it does not mean that this infection is harmless. It is also capable of encrypting files, as our malware analysts have found. Delete CryptoKill Ransomware as soon as possible because keeping a ransomware infection installed on the computer is a really bad idea.
Once CryptoKill Ransomware ends up inside the computer, it encrypts files in only one folder (%USERPROFILE%\Documents\test), if it finds it, and then opens a window containing a message. It tells users that their files have been encrypted with CryptoKill Ransomware. It becomes clear after reading this message that it does not call itself a ransomware infection. Instead, it presents itself as “a new kind of cryptography malware.” Unlike other ransomware infections, it does not provide further instructions on how to decrypt files, i.e. it does not offer to purchase a special decryption key to unlock the encrypted files. Users are only told instead that CryptoKill Ransomware uses a unique one-way encryption key which might be impossible to crack. What it tries to tell users is that it might be impossible to get files back. In this sense, this infection can be called unique because ransomware infections are usually developed by cyber criminals to easily obtain money from people. The red window containing the message is not the only one this malicious application leaves for users. If CryptoKill Ransomware finds a test folder in %USERPROFILE%\documents, it also places a CRYPTOKILL_README.txt file containing a message similar to the one placed in a window on Desktop. As has been mentioned, only one folder is affected by this ransomware infection, so users who get infected with it might not find any encrypted files if this folder does not exist on their computers. In this case, the deletion of this computer infection is still a must.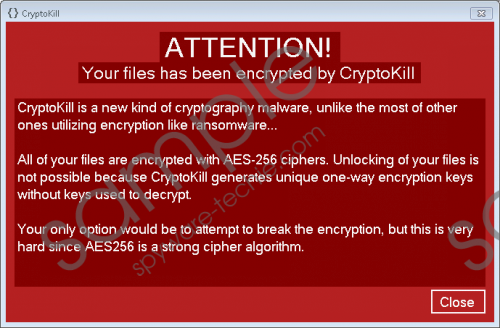 CryptoKill Ransomware screenshot
CryptoKill Ransomware screenshot
Scroll down for full removal instructions
CryptoKill Ransomware is not an extremely popular computer infection yet, and cyber criminals might stop distributing it soon, but users should still know how it is usually spread so that they could prevent this threat from entering their PCs. Research has shown that this ransomware infection usually pretends to be a harmless attachment and is spread through malicious emails the most frequently. Theoretically, it might find other ways to enter computers too, so users should have a security tool installed on their computers. Do not forget to stay away from spam emails after the installation of an antimalware application as well.
Users can get rid of CryptoKill Ransomware quite easily because this infection can be fully removed by deleting the suspicious recently downloaded file and the test folder from %USERPROFILE%\documents, if it exists. Therefore, users should not waste time and go straight to delete it. If this infection is left on the computer, it might be updated one day and start encrypting files placed in other directories too. Other malicious applications might enter computers easier because of the presence of this ransomware infection too.
Delete CryptoKill Ransomware
- Open the Windows Explorer (Win+E).
- Go to %USERPROFILE%\Downloads and %USERPROFILE%\Desktop.
- Find the malicious file recently downloaded and delete it.
- Pay a visit to %USERPROFILE%\Documents.
- If you can find the test folder there, delete it.
- Empty the Recycle bin.
In non-techie terms:
CryptoKill Ransomware encrypts files in only one folder, but it does not mean that it is safe to keep it on the computer, so users who ever find its window with a message opened on their screens should go to erase the ransomware infection from their PCs as soon as possible. Since this infection, theoretically, might not be the only one performing activities on the system, it would be smart to scan the computer with an automatic malware remover too. It will take care of all other threats quickly.
