Do you know what CryptoHost Ransomware is?
There is no doubt that CryptoHost Ransomware is a creation of cyber criminals, and you should realize this as soon as this infection corrupts your computer. Also known as Manamecrypt Ransomware, this infection encrypts your personal files and demands a ransom using a screen-size notification. The developer of this ransomware does not hide its objective, which is to get your money, which is why we are sure that you will realize being held hostage by cyber criminals. Of course, it is not you that is held hostage per se, but rather your personal files. According to our research, JPG, JPEG, PNG, GIF, AVI, MOV, MPEG, M4V, PDF, DOCX, and other types of files could be encrypted by this threat. Although it encrypts files, it acts differently than CryptoJoker Ransomware, Locked Ransomware, and other infamous infections that we have analyzed in the past. If you want to learn about that, and you are interested in removing CryptoHost Ransomware, please continue reading.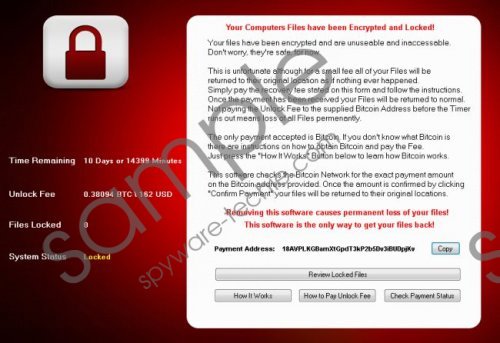 CryptoHost Ransomware screenshot
CryptoHost Ransomware screenshot
Scroll down for full removal instructions
According to our research, CryptoHost Ransomware is spread via malicious websites along with µTorrent. Of course, other programs could be offered along with this threat, and you will be unaware of that because the installer of this ransomware is silent. Due to this, you MUST be careful when downloading software; otherwise, you are at risk of letting in serious infections without even knowing it. Once installed, this infection checks for certain types of files (some of them are mentioned above) and moves them into a RAR archive protected with a password. This folder is most likely to be located in the %AppData% directory. The password is what CryptoHost Ransomware uses to extort money from you, as you need it to access your personal files, but you do not actually need to pay the ransom to retrieve this password. The name of the archive, which consists of 41 random numbers and letters, is part of the password, while the other part of the password is your own windows username. “B69CC4A91E86934CFD0753D5E928F1E026222D0Busername” is an example of a password that might help you retrieve your personal files. If you are not sure what your username is, go to C:\Users\ and check for folders that show your username (e.g., User).
Computer users who do not seek for help and do not research CryptoHost Ransomware might be pushed into following the demands of cyber criminals. Although the pop-up notification presented by this infection suggests that a “small fee” can help you retrieve your files, this fee is not that small. In our case, a sum of 0.38094 Bitcoins, or 162 USD, was requested. Bitcoin is a virtual currency that you need to purchase first, which makes the process a little more complicated, but, at the end of it, schemers can collect money in an easier and safer manner. Furthermore, this infection can show warnings (see an example below) urging you to pay money when you browse the web. This infection checks for certain strings in the names (e.g., facebook, instagram, youtube, vimeo) of the sites you visit, as well as processes (e.g., anti-virus, antivirus) to abort its own process called “CryptoHost.exe” or to point back to the ransom payment. On top of that, the main pop-up discourages you from taking any action other than paying the ransom suggesting that your files will be permanently lost otherwise.
Warning
[URL] – Internet Explorer Is not allowed to function until the fee is paid.
You need to delete CryptoHost Ransomware from your computer regardless of whether or not you pay the ransom. Hopefully, you are reading this report in time, and you learn how to retrieve the password before paying any money. If you follow the instructions below, you will learn how to eliminate this infection from your operating system, but this is not the last step you should make. Additionally, you should immediately install an anti-malware tool to ensure further protection and to completely clean your operating system. Although this ransomware is extremely malicious and annoying, more silent and inconspicuous infections active on your PC could be just as dangerous, and a reliable security tool will find and delete them.
Remove CryptoHost Ransomware
- First download a tool (e.g., WinZip) capable of extracting RAR archives (if you cannot download one from the infected PC, download it using a “healthy” machine, and transfer it using, for example, a USB drive).
- Launch the Explorer window using the Win+E combination (tap these keys together).
- Enter %AppData% into the address bar.
- Find the archive file whose name consists of 41 random symbols.
- Extract the file and enter the password that is the combination of the 41-symbol file name and your username (e.g., B69CC4A91E86934CFD0753D5E928F1E026222D0Busername).
- Move to the folder containing the extracted files and back them up.
- Launch Task Manager (Ctrl+Alt+Delete/Ctrl+Shift+Esc) and move to the Processes tab.
- Terminate the process called CryptoHost.exe and exit the Task Manager.
- Launch Explorer and move to the %AppData% directory again.
- Right-click and Delete the cryptohost.exe file.
- Now launch RUN (simultaneously tap Win+R) and enter regedit.exe.
- Navigate to HKCU\Software\Microsoft\Windows\CurrentVersion\Run.
- Right-click and Delete the value called “software” (value data: %AppData%\cryptohost.exe).
- Navigate to HKCU\Software\Classes\ and Delete the FalconBetaAccount key.
- Delete the malicious Torrent file that unleashed CryptoHost (e.g., %Temp%\uTorrent.exeuTorrent.exe).
In non-techie terms:
CryptoHost Ransomware is an infection, and you need to remove it from your Windows operating system as soon as possible. Remember that if you have paid the ransom – and you do not need to do that – you still need to remove this malicious ransomware. If you are still dealing with this threat, use the guide above to learn how to retrieve the files “encrypted” by this threat. Afterward, employ legitimate security software to ensure reliable, full-time protection. If you postpone the installation of this software, other dangerous threats could slither in very soon, and you can prevent that easily using the right anti-malware software.
