Do you know what CryptoGod Ransomware is?
CryptoGod Ransomware may have been created by hackers from Italy; our researchers say it is possible since the Italian language was used in the malicious application’s source code. From looking at the malware’s code and testing the program on our internal lab, our specialists learned quite a lot about the infection, and if you keep reading this report, you will get to know it better as well. However, if you are only interested in how to delete it from the computer, we recommend following the removal guide placed below the article. At this point, we should mention the CryptoGod Ransomware’s deletion will not undo the damage it did to the user’s personal files. Sadly, all affected data would remain encrypted even if the threat is no longer on the system. Nonetheless, there are a couple of methods that could help you recover some part of enciphered files, but we will mention them later in the text.
Users could accidentally infect their system with CryptoGod Ransomware while using installers downloaded from malicious web pages or opening suspicious email attachments. Afterward, the malware should begin enciphering private data without any delays, unless the victim has a reputable antimalware tool that can stop the threat. During the encryption process, each file might be marked by an additional .payforunlock extension. Then, the malicious program should open a pop-up window containing the message from the cyber criminals who developed this infection. This pop-up message is their ransom note, and as expected it demands the victim pays a ransom.
The requested amount is 0.03 Bitcoins; converted to US dollars the sum stands for approximately $75. It may not seem significant, but given the victim could lose it in vain, we believe the user should consider this option with care. There is a chance they could take your money without delivering the promised decryption tools. Plus, by paying the ransom, you would fund the cyber criminals. Thus, instead of putting up with any demands, we encourage you to remove CryptoGod Ransomware. Once the system is clean, you could try special recovery tools or switch enciphered files with unaffected copies available on a flash drive, external hard drive, and so on. The only question is how can one get rid of such a dangerous threat?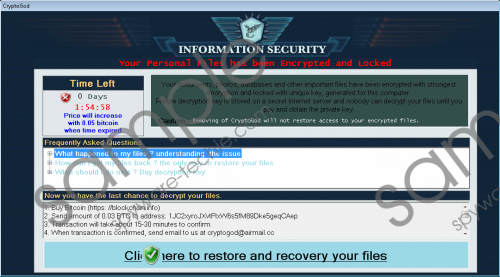 CryptoGod Ransomware screenshot
CryptoGod Ransomware screenshot
Scroll down for full removal instructions
The malicious application settles on the system by creating a copy of itself in %AppData%\MoWare_H directory. The MoWare_H folder and whole data on it belong to the infection. If you check your Registry Editor, you should also find a value name called CryptoGod. No doubt it is created by CryptoGod Ransomware. It seems the value name’s data points to the mentioned copy located in %AppData%\MoWare_H\My\1.0.0.0 directory. Its purpose is to run the malware when you close its window or restart the infected computer. What’s more, it was noticed that the malicious program could disable the user’s Command Prompt, Registry Editor, and Task Manager. As you may imagine, erasing data associated with the threat or simply using the infected computer might become impossible.
Luckily, we know how to enable your Task Manager and other important system’s features. All you have to do is follow the removal guide we placed at the end of the main text carefully, and you should not only enable necessary features but also eliminate the malware. Needless to say, the process might take some time, and for some of you, it could be too difficult to handle. Provided that is the case for you, we advise not to waste any time and use a reputable antimalware tool instead. It should be able to restore disabled features and erase CryptoGod Ransomware too, but it would allow you to do so automatically.
Enable Registry Editor
- Click the Windows button.
- Type gpedit.msc in the operating system’s search box and click Enter.
- Search for this path: User Configuration\Administrative\Templates\System
- Select Prevent access to registry editing tools.
- Choose Disabled or Not Configured.
- Tap OK.
Enable Windows Task Manager
- Press the Windows button.
- Type gpedit.msc in the search box and launch gpedit.
- Navigate to the provided location: User Configuration\Administrative\Templates\System\Ctrl+Alt+Del Options
- Select Remove Task Manager.
- Choose Disabled or Not Configured.
- Press OK.
Enable Command Prompt
- Click the Windows button.
- Type gpedit.msc in the search box and press Enter.
- Search for this location: User Configuration\Administrative\Templates\System
- Mark Prevent access to the command prompt.
- Select Disabled or Not Configured.
- Press OK.
Get rid of CryptoGod Ransomware
- Press Ctrl+Alt+Delete at the same time.
- Select Task Manager and go to the Processes tab.
- Search for a process titled as CryptoGod.exe, mark it and click End Task to kill it.
- Exit the Task Manager and press Windows Key+E.
- Check the provided directories:
Desktop
Temporary Files
Downloads - Locate the malware’s launcher.
- Select this file, right-click it and mark Delete.
- Search for this folder: %AppData%
- Pick a folder titled as MoWare_H, right-click it and press Delete.
- Leave the File Explorer.
- Press Windows Key+R, type Regedit, and tap Enter.
- Find this location: HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- Choose a value name called CryptoGod, right-click it and pick Delete.
- Exit the Registry Editor and empty your Recycle bin.
- Restart the computer.
In non-techie terms:
CryptoGod Ransomware is a malicious program every user would like to avoid, but if you did encounter it, we recommend erasing it from the system without any delay. Especially if you do not wish to gamble with your money, by trying to purchase the decryption tool from the malware’s creators. The cyber criminals who develop such threats cannot be trusted and some users who make the choice of paying the ransom later bitterly regret it when they get scammed. If you do not wish to find yourself in such situation, we urge not to hesitate anymore and take control of the PC with the removal guide located above or a reputable antimalware tool.
