Do you know what CryptConsole v3 Ransomware is?
CryptConsole v3 Ransomware (also known as Cryptoconsole-2018) is the newest variant of Cryptoconsole Ransomware. It is considered a harmful malicious application like its predecessor because it locks users’ personal files without mercy once it successfully slithers onto their computers. It uses the AES encryption to lock victims’ files, which means that it might be problematic to unlock them. Cyber criminals are aware of this fact, i.e. they have set CryptConsole v3 Ransomware to lock files with a strong cipher not without reason – they want users to purchase the decryptor from them. There is a possibility that there are no other ways to unlock encrypted files, but you should still not purchase the decryption tool from cyber criminals. We say so because a) you do not know whether such a tool is available and b) there are no guarantees that cyber criminals behind CryptConsole v3 Ransomware will give it to you. No, you could not get your money back in this case. No matter what you decide to do, make sure you do not keep the ransomware infection active on your computer. Our team of experienced malware analysts says that this infection should not create entries in the system registry or drop a separate folder with malicious files. Because of this, its removal should be relatively easy too.
Unlike some other typical ransomware infections, CryptConsole v3 Ransomware does not change the extension of those files it encrypts. Instead, you will find their names changed to a jumble of letters and numbers, for example, 70726F636573636861636B65722D322E33392D73657475502E657865 and 4449952E6C6E6B. According to researchers who have analyzed this threat, other variants of this malicious application that rename files differently might exist too. The ransomware infection does not leave users in a state of ignorance. It drops README.txt on Desktop after locking data found on the affected computer. You can send one file to avira@keemail.me or starbax@tutanota.de to get it decrypted for free. Even if cyber criminals send you the decrypted file, it does not mean that they will unlock all other files for you too. Because of this, we cannot let you transfer money to them. It does not mean that there are no other ways to restore encrypted files. If you cannot find a free decryptor, you should replace encrypted files with those from your backup. Of course, you have to remove the ransomware infection first.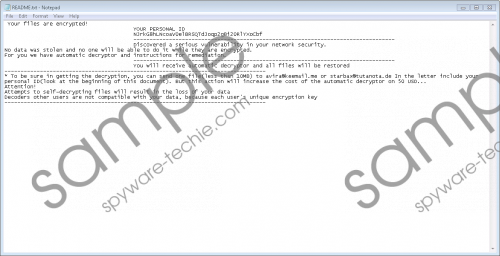 CryptConsole v3 Ransomware screenshot
CryptConsole v3 Ransomware screenshot
Scroll down for full removal instructions
All users check their emails once in a while. The next time you do that make sure you do not open any suspicious emails or their attachments because it is very likely that you have installed CryptConsole v3 Ransomware on your PC by doing this. Keep in mind that even emails from legitimate-looking companies might contain malicious software, so it is very important to inspect them closely before opening attachments they hold. We cannot promise that it is the only way this malicious application is spread. According to researchers, this infection might also be distributed differently. For example, you might download it from a file-sharing website. If you do not think that you could prevent harmful infections from entering your system illegally all alone, install a reputable antimalware tool on your computer. Your PC will be protected as long as you keep this tool installed and enabled.
You must remove CryptConsole v3 Ransomware from your system ASAP if you have discovered it installed so that it could not lock more files on your computer. You do not need to be an expert in malware removal to erase it yourself manually because your only task will be to locate and delete the malicious file. Once it is gone, delete the ransom note dropped. You can erase CryptConsole v3 Ransomware automatically instead if you want to, but do not expect an automated malware remover to unlock encrypted data for you.
How to delete CryptConsole v3 Ransomware
- Open Explorer.
- Locate and then delete the malicious file launched (check the following directories: %USERPROFILE%\Downloads, %USERPROFILE%\Desktop, %TEMP%, and %APPDATA%).
- Remove README.txt.
- Empty Trash.
- Perform a system scan with a diagnostic antimalware scanner.
In non-techie terms:
Ransomware infections are nasty threats designed to lock personal files (e.g. documents, images, and music) and swindle victims out of their money. This malicious application does not differ much from similar threats, so it should be mainly distributed as an email attachment inside spam emails. Of course, if you keep downloading programs from dubious file-sharing websites, you might find it installed on your computer too. Do not let this happen to you.
