Do you know what Crypren Ransomware is?
If your data was encrypted by Crypren Ransomware, it is time to learn more about this Trojan infection. This malware is rather typical compared to other similar threats. It uses a particular cryptosystem to lock your data and demands you to pay the ransom if you want to use your files again. The ransomware asks you to pay 0,1 Bitcoins, which is 45,61 US dollars at the moment. The sum is quite small, but you do not have to put up with these demands. We prepared a removal guide below, so you can get rid of the malware. Sadly, its deletion will not decrypt your files, but there are reports of decryptor that is available on the Internet. We cannot say how much it could actually help you, but you should know it exists. It is entirely another case if you have copies of your files on some removable media device because then you do not have to worry that your data could be lost.
Our researchers say that Crypren Ransomware could spread through malicious email attachments. Once you open such a file, it might release a Trojan that could drop the ransomware on your system. In many cases, the malicious attached files look like simple text documents. Also, they have titles that provoke user’s curiosity. Maybe you recall opening any suspicious file before your data was encrypted? If your answer is yes, you should avoid questionable email attachments in the future.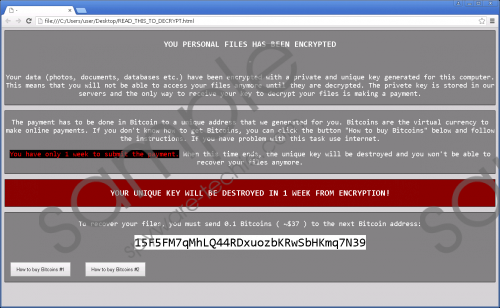 Crypren Ransomware screenshot
Crypren Ransomware screenshot
Scroll down for full removal instructions
Crypren Ransomware locks your data using the AES-256 encryption algorithm. Afterward, all encrypted files should have an additional extension that is particular for this ransomware, e.g. picture.jpg.encrypted. We noticed that this malware targets personal user’s data. For instance, it should encrypt files that have the following extensions: .doc, .docm, .docx, .docxml, .docz, .gif, .gzip, .html, .jpg, .jpg2, .mdb, .mp3, .mp4, .mp4infovid, .mp4v, .pdf, .php, .php3, .png, .ppt, .pptm, .pptx, .py, .rar, .rar5, .rb, .rtf, .sql, .sqlite, .sqlite3, .sqlitedb, .swf, .swfhtml, and many others.
Furthermore, the malicious program creates an HTML file called something like “READ_THIS_TO_DECRYPT.” The file is placed in every folder which contains encrypted data. One more copy is in the Startup directory. If you launch the file, it will load a web page on your browser. Mainly, this site contains a note from the Crypren Ransomware infection’s creators. It says that the only way to get your data back is to pay the ransom. To make you even more scared, it warns you that you have to make the transfer in 7 days, or your unique decryption key will be destroyed.
If you do not have a backup for the files that were encrypted, it might seem like you have no other choice but to pay the ransom. However, there may be a working decryptor on the Internet, and you could try using it to unlock your data. Of course, it is your choice, but do not forget that cyber criminals cannot be trusted. It is possible that they will not provide the decryption key, so no matter how small the ransom might be , it could be lost together with your data as well.
If you decide to eliminate Crypren Ransomware, we will help you get rid of it with the instructions provided below the text. Firstly, you should erase the ransomware’s executable file from the %ALLUSERSPROFILE% directory. The executable file should have a random name, so we cannot say what it is called on your system. Lastly, you should remove all HTML files placed by the malicious program. If this is too complicated for you, there is another way to eliminate the malware. You could use a reputable security tool that should find all data that belongs to the infection and erase it.
Eliminate Crypren Ransomware
- Open the Explorer (Windows Key+E).
- Navigate to: %ALLUSERSPROFILE%
- Find the ransomware’s executable file with a random title.
- Right-click it and select Delete.
- Go to: %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
- Find HTML file named as READ_THIS_TO_DECRYPT.html and right-click to delete it.
- Erase all other HTML files on your computer.
- Close the Explorer and empty your Recycle Bin.
In non-techie terms:
Crypren Ransomware demands a rather small amount of Bitcoins compared to other similar infections, but paying the ransom should be your last resort. Firstly, you should try available decryptors on the Internet or specific software that could be able to recreate some files. If you erase the ransomware manually, you should still scan your computer with a reliable antimalware program. It will eliminate any other threats that might have entered your system. Also, you should consider backup options for your future files, so that next time you could remove malware without any hesitation.
