Do you know what Cryakl Ransomware is?
Cryakl Ransomware is a typical ransomware-type infection but one that needs an in-depth analysis nonetheless. From the outset, we advocate for removing this infection instead of paying the ransom that its developers want you to pay for the decryption key. The thing is, its developers might not send you the key on purpose as all they care about is making money. However, there is no way of decrypting the files using a third-party decryption tool either because it does not exist and it is unlikely that it will even do because this ransomware’s encryption is very strong.
This ransomware uses a hybrid AES and RSA encryption algorithm with a 2048-bit key length. Therefore, this encryption is very hard to break, if not impossible. While encrypting, this ransomware has been configured to add eemail-iizomer@aol.com or ninja.gaiver@aol.com email address to the beginning of the file name and the .cbf file extension at the end. Furthermore, it is capable of encrypting almost all file types, so this means that it can also encrypt your documents, images, videos, audio files and so on. docx, .doc, .odb, .odc, . png, .jpeg, .txt, .rar, .m4a, .wma, and .avi are just a handful of file formats that can be encrypted by this ransomware.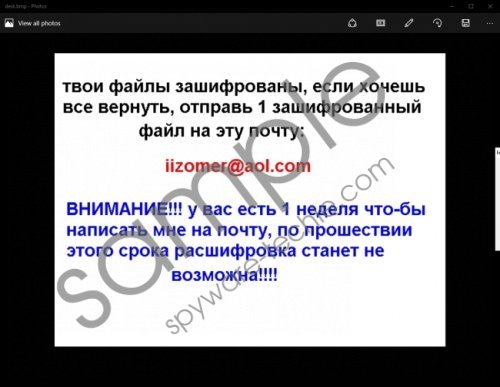 Cryakl Ransomware screenshot
Cryakl Ransomware screenshot
Scroll down for full removal instructions
Once your files have been encrypted, your desktop wallpaper will be changed to an image that acts as the ransom note. However, the note is in the Russian language so it may be unintelligible. The ransom note states the obvious — your files have been encrypted, and you need to write an email to iizomer@aol.com or gaiver@aol.com. The ransom asks you to send one encrypted file to the cyber criminals within a week, or your files will remain encrypted forever. The criminals should also provide you with instruction on how to pay the ransom. They will most likely ask that you pay it in Bitcoins as other payment methods can be traced to the criminals.
According to our researchers, Cryakl Ransomware is set to drop its main executable either in %TEMP%, %PROGRAMFILES% or %PROGRAMFILES(x86)%. The main executable is named service.exe, but the name can be random as well. Furthermore, this malicious application will create a registry string in HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run which is referred to as the point of execution. The string is named pr and its value data should look something like C:\Program Files (x86)\service.exe, for example. You have to delete these files to restore your computer’s security. However, before we get to that, let us discuss how this ransomware is distributed.
Our security analysts have discovered that Cryakl Ransomware is being disseminated via email spam. They say that the emails are disguised as business correspondence, and they contain text that says the following:
Dear client,
Our finance department has processed your payment, unfortunately it has been declined. Please, double check the information provided in the invoice down below and confirm your details.
Thank you for understanding.
We warn you that this invoice is fake, and it will run Cryakl Ransomware when you open it. The mail spam is set to random email addresses, so this kind of email can be sent to you as well. A power antimalware tool such as SpyHunter can prevent this infection from entering your PC entirely.
If your computer has been infected with this ransomware, then we recommend that you remove it using either our manual removal guide or our featured antimalware program. We urge you not to pay the ransom because the cyber criminals might not keep their word and give you the decryption key.
How to delete this infection
- Hold down Windows+E keys.
- Enter the following paths into the address box.
- %PROGRAMFILES%
- %PROGRAMFILES(x86)%
- %TEMP%
- Locate service.exe (name can be random) and delete it.
- Close the window.
Delete the registry key
- Windows+R keys.
- Type regedit in the box and click OK.
- Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Find and delete the value name pr (contains value data such as C:\Program Files (x86)\service.exe)
In non-techie terms:
Cryakl Ransomware is a Russian-made infection se to encrypt the files on your computer and demand that you pay a ransom in return for the decryption key needed to decrypt them. It uses a strong encryption algorithm at is nearly impossible to decrypt, but we urge you to refrain from paying the ransom because the criminals might not give you your files back. Please use SpyHunter or the guide above to delete this infection.
