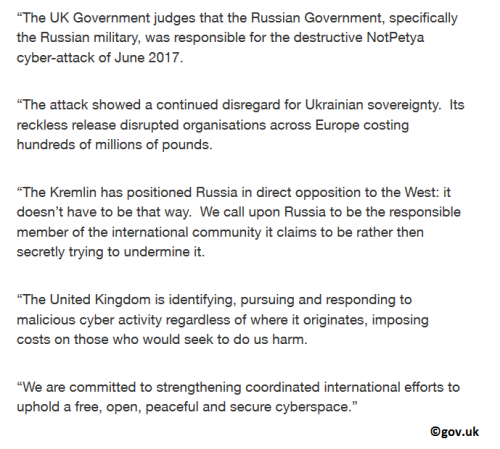
The UK Government investigated the attacks of the infamous NotPetya Ransomware that occurred in June 2017. The conclusion is that the Russian government stands behind the malicious infection. Lord Ahmad of Wimbledon – who is the Foreign Office Minister – used the official government’s website to accuse the Russian Government of using NotPetya for direct attacks against Ukraine and numerous European organizations and companies. The notes supporting the statement indicate that the UK’s National Cyber Security Centre has proof suggesting that the Russian military participated in the attack. The image below represents all statements made by the Foreign Office Minister.
This is not the first time a government-level agency has concluded that Russia was somehow involved. Back in January 2018, reports emerged suggesting that the Central Intelligence Agency (CIA) conducted an investigation that resulted in the same conclusions. A month later, the Press Secretary presented a statement supporting the findings by stating that the NotPetya Ransomware attacks were “part of the Kremlin’s ongoing effort to destabilize Ukraine and demonstrates ever more clearly Russia’s involvement in the ongoing conflict.” The Australian Government was quick to join in as well stating: "Based on advice from Australian intelligence agencies, and through consultation with the United States and United Kingdom, the Australian government has judged that Russian state sponsored actors were responsible for the incident."
In June 2017, the sophisticated NotPetya Ransomware was silently spread using the software update of Ukraine-based M.E.Doc. The infection was targeted at big companies and organizations, such as the container shipping giant, Maersk. According to the company, the NotPetya Ransomware attack cost it between $250-300 million in losses. Unfortunately, the ransomware, in many cases, wiped data instead of encrypting it, which meant that recovering files was not possible at all. Also, in other cases, the threat would corrupt the MBR (Master Boot Record), making it impossible to access the operating systems altogether. The companies and organizations dealing with the malicious NotPetya Ransomware were not only suffering from the loss of data but, in many cases, the loss of control altogether. Reinstalling systems and getting back on track disrupted many companies, which ended up costing them a lot of money. This is truly unfortunate, considering that the threat was dispersed using a known Windows SMB vulnerability. If you want to learn more about this infection, read a full report here.
Although it has been proven time and time again that the creators of ransomware infections are very smart and very quick to exploit any security vulnerability they can find, there are things that companies can do to prevent attacks in the future. First and foremost, it is important to ensure all-rounded protection, and this might be impossible without open communication between government-level agencies, malware analysts, and the companies who are likely to be targeted. The sooner everyone learns about the security backdoors and ways to patch them, the fewer chances cyber attackers will have to successfully bring their victims to their knees. Backing up data is also imperative because, in many cases, it is impossible to recover the corrupted data, and it can be restored using backups only. Big companies should also start investing more money into virtual security because infections like NotPetya Ransomware will not disappear. On the contrary, more of them are likely to emerge; especially considering the political tension between the East and the West.
References:
F&CO, NCSC, and Lord Ahmad or Wimbledon. February 15, 2018. Foreign Office Minister condemns Russia for NotPetya attacks. GOV.UK.
Nakashima, E. January 12, 2018. Russian military was behind ‘NotPetya’ cyberattack in Ukraine, CIA concludes. The Washington Post.
Press Secretary. February 15, 2018. Press Secretary Statement. The White House.
The Hon Angus Taylor MP. February 16, 2018. Australian Government attribution of the ‘NotPetya’ cyber incident to Russia. Department of Home Affairs.