Do you know what Cocoslim98@gmail.com Ransomware is?
It is not very difficult to figure out if Cocoslim98@gmail.com Ransomware has slithered in. Immediately after infiltration, this infection encrypts your personal files and adds a unique extension to their names. This unique extension includes an email address, and that is the only piece of information that this threat provides its victims with. Our research team has found that there are two different versions of this infection. One of them represents the cocoslim98@gmail.com email address, and the other one uses glok9200@gmail.com. The added file extensions also include “.tar”, which is an archive file type on Linux operating systems. The ransomware does not archive your files, and that is just a combination of random letters. Once you discover the infiltration of malware, immediately inspect which files were encrypted. In the best case scenario, you will discover that the most important files hit by this malware are backed up, in which case, nothing should stop you from deleting Cocoslim98@gmail.com Ransomware.
These are the types of files that Cocoslim98@gmail.com Ransomware attempts to encrypt: .3gpp2, .acc, .apc, .cache, .cfg, .chm, .conf, .dat, .def, .dtd, .exp, .gif, .h, .html, .ini, .isl, .jcp, .jrs, .js, .json, .jtx, .little, .lua, .mozlz4, .odt, .png, .pset, .reg, .sbstore, .sqlite, .txt, .uca, .xml, and .zip.
When Cocoslim98@gmail.com Ransomware encrypts the files that it is set up to target, no additional files are created to introduce you to the ransom demands. This is quite odd, considering that most ransomware infections, such as Screenlocker Cuzimvirus or Princess Locker Ransomware, create files that represent different demands. The creator of Cocoslim98@gmail.com Ransomware expects you to figure out that you need to email them just by looking at the names of the encrypted files. If you figure that you, cyber criminals should send you an email asking to pay a ransom. You might be provided with the option to decrypt a few files for free just to see if cyber criminals are capable of decrypting your personal data. The ransom fee requested by the infection might be different in every case, but it is most likely that you will be asked to pay a lot of money for the decryption of your files, and that does not change by removing the threat.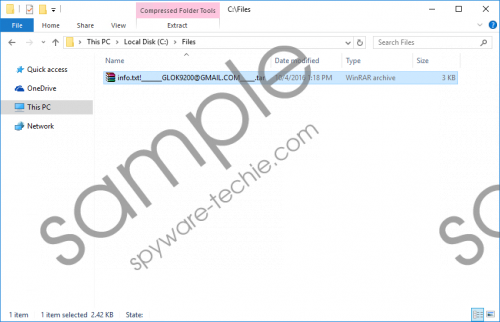 Cocoslim98@gmail.com Ransomware screenshot
Cocoslim98@gmail.com Ransomware screenshot
Scroll down for full removal instructions
Are the files encrypted by Cocoslim98@gmail.com Ransomware worth the ransom fee they are asked for? If they are not, why are you even thinking about paying the ransom? Now, if your files are too precious to lose, you might be willing to take the risk. Why do we consider paying the ransom a risk? That is because the ransom and the decryptor are controlled by cyber criminals. If they receive the ransom, they already have what they want, and they have absolutely no obligation to give you the decryptor. What could you do if you got scammed? Flood cyber criminals with intimidating emails? We are sure that that would not work. Ignoring the request to pay the ransom might not play out well either. Overall, there is not much anyone can do once the ransomware takes over your files. If you are unable to find a legitimate file decryptor, you might have to remove the infection without recovering your files first.
The instructions below were created to guide users with the manual removal of Cocoslim98@gmail.com Ransomware. Are you ready to take on this task? If you are not, you can download an anti-malware tool instead. In fact, this is the better choice, considering that the right tool can eliminate all malicious threats at once and keep the system protected against new incoming infections as well. If you have additional questions about the infection or its removal, please start a conversation below.
Delete Cocoslim98@gmail.com Ransomware
- Simultaneously tap keys Win+E to launch Explorer.
- Type %LOCALAPPDATA% (type %USERPROFILE%\Local Settings\Application Data\ if you use Windows XP) into the Explorer’s bar to access the directory and tap Enter.
- Right-click the folder named PeerDistRepub and choose Delete.
- Type %Temp% into the bar and tap Enter.
- Right-click and Delete the malicious .exe file that should be originally located in the PeerDistRepub folder.
- Now, check all of these directories to find and Delete the malicious .lnk file linked to the .exe file:
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\
- %USERPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup\
- %ALLUSERSPROFILE%\Start Menu\Programs\Startup\
- %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Startup\
- %ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs\Startup\
In non-techie terms:
Postponing the removal of Cocoslim98@gmail.com Ransomware would be a mistake, which is why we strongly recommend taking action right now. This ransomware is very devious because it does not leave any other option for its victim but to pay the ransom. Of course, the victim also has the option to lose the personal files. Considering that this infection demands a huge ransom fee, it is unlikely that many users will pay it. The truth is that we would not advise paying the ransomware even if it was small because there are absolutely no guarantees that cyber criminals would keep their promises to unlock your files. Install automated malware removal software to eliminate the ransomware, as well as other infections that might be active, or use the guide above to initiate the removal process manually.
