Do you know what Cockblocker Ransomware is?
A new malicious application Cockblocker Ransomware has been detected by cyber criminals recently. It is evident that it is still in development because it does not always encrypt files and does not leave a ransom note with instructions on how to decrypt files. Of course, a new fixed version of Cockblocker Ransomware might be released in the future, so the information you find here might be already outdated at that time. No matter which version of Cockblocker Ransomware you encounter, make sure you delete all the components of this infection from the system. Fortunately, it does not create a point of execution, block system utilities, or lock the screen, so your only job will be to detect and delete the malicious file launched. If this file is not removed from the computer, there is a risk of launching it again and, consequently, finding personal files encrypted.
When this ransomware infection is launched, a pop-up window containing OK and a Command Prompt window show up. If you encounter a version encrypting files, i.e. working properly, you will see lines similar to this one C:\Users\Public\Music\song.mp3 in the CMD window. This means that files are being encrypted. Once Cockblocker Ransomware finishes doing that and a user clicks OK in the pop-up window, another window with a title RansomwareDisplay appears. It has a text full of mistakes: “Yo file’s been encrypted nigga Pays me a bitcoin and I unencrypt them fam” and two boxes (Encrypted Files and Use Decryption Code). Since Cockblocker Ransomware does not lock the screen, this window can be closed by clicking X. Unfortunately, we cannot say the same about the files encrypted by Cockblocker Ransomware – it will definitely not be easy to decrypt them.
If you encounter a version of Cockblocker Ransomware that encrypts files, you will find that it is impossible to access pictures, music, documents, and other valuable data very quickly. All these encrypted files will have a new filename extension .hannah, so it will not take long to find out what has happened to them. Since there is no information about the decryption of files provided in the ransom note opened after the encryption process is finished, it means that cyber criminals will not give you the key to unlock your files. What you can do instead of trying to get this key is to recover files from a backup after the full deletion of Cockblocker Ransomware. Alternatively, you can use a free data recovery tool. This application can be downloaded from the web, but, unfortunately, we cannot guarantee that it will unlock files for you. Last but not least, you can wait for specialists to develop the free decryptor. Since Cockblocker Ransomware uses a very strong RSA encryption algorithm, it might take some time for them to create the decryption tool.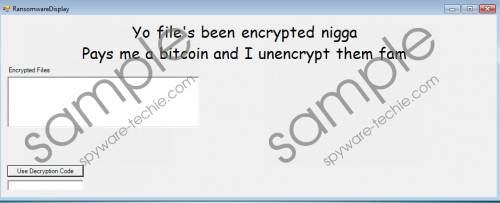 Cockblocker Ransomware screenshot
Cockblocker Ransomware screenshot
Scroll down for full removal instructions
Before we provide more information about the removal of Cockblocker Ransomware, we want to tell you how ransomware infections are usually distributed. We hope this knowledge will help you to prevent similar infections from entering the computer in the future. According to our research team, these threats enter computers illegally, but users help them to do that without even realizing that. If you wonder how users contribute to the entrance of malicious software, you should know that they tend to open spam email attachments. These attachments do not look harmful at first glance (e.g. an attachment might look like an important document), so users open them fearlessly. Keep in mind that it is a common but not the only ransomware distribution method, so it is highly recommended to be more careful and thoughtful. On top of that, it would be smart, according to our security specialists, to install a security application. If you do not forget to keep it enabled on your computer, malicious software will never find a way how to enter your system again.
As has already been mentioned, Cockblocker Ransomware does not copy itself to different places, does not make modifications in the system registry, does not create a point of execution, and does not lock the screen. As a consequence, you will only need to delete the malicious file you have launched. Unfortunately, this will not be very easy to do because you will have to find that malicious file yourself. If it is impossible, use a reputable automated malware remover, e.g. SpyHunter. It will also delete other malicious components you know nothing about. The only thing it is not going to do is to unlock files encrypted by Cockblocker Ransomware.
Delete Cockblocker Ransomware
- Press Win+E.
- Go to %TEMP% and %USERPROFILE%\Downloads.
- Find the malicious file you have recently launched.
- Delete it.
- Clear the Recycle bin.
In non-techie terms:
If you have found the malicious file and already deleted it, it does not mean that your PC is clean now. Specialists say that there might be a bunch of other infections that are working in the background without your consent installed on the system, so it is a must to scan the computer against malicious software with an automatic tool too. Use only a reputable scanner.
