Do you know what Cerber2 Ransomware is?
Cerber2 Ransomware is the second iteration of the infamous Cerber Ransomware that was all over the Internet infecting many computers only a few months back. Like its predecessor, this new infection is set to encrypt your files and demand that you pay a ransom. However, recommend that you remove this infection instead of paying the ransom because it will only encourage the cyber crooks to release the third version of it. Note that at the time of this article there was no free decryption tool for this ransomware. Still, if there is such a tool, you have to get rid of this ransomware first to use it. We are going to cover the most relevant information about Cerber2 Ransomware, so, without further ado, let us begin.
Like its predecessor, this new version is also being distributed on an underground Russian forum that is not accessible to the general public. Hence, only those with the right connections can get a hold of this ransomware. Indeed, it seems that it is being sold as a Ransomware as a Service (RaaS) so cyber criminals can purchase it and distribute it in any manner they choose. It is possible to distribute this ransomware via email spam that contains a dropper file that places this ransomware’s files onto your PC secretly. Regardless of the distribution method, this infection can enter your PC without your knowledge. Even if you have an antimalware program that can stop Cerber Ransomware, it might be ineffective against Cerber2 Ransomware. Nevertheless, our security experts have determined that SpyHunter is capable of detecting and preventing both of these malicious applications from infecting your PC. Not only that but it can remove them if you installed it after the infection has already taken place.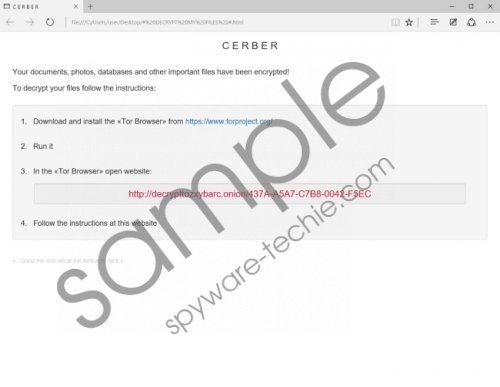 Cerber2 Ransomware screenshot
Cerber2 Ransomware screenshot
Scroll down for full removal instructions
However, Cerber2 Ransomware will not work in certain countries. Our researchers say that it has a blacklist of countries that include Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine, and Uzbekistan in which this infection does not work. The ransomware connects to the Internet and determines in which country it is located and then takes actions accordingly.
Cerber2 Ransomware is set to drop its malicious randomly named executable is a randomly named folder located in %AppData%. The folder that it is configured to be placed in named like a CLSID. The computer will restart in Safe Mode with Networking after the infection is complete. Then, it will generate a fake “You are about to be logged off” message. Your computer will restart and boot into normal mode after you close this message. However, when your computer boots up in normal mode, this ransomware will start the encryption process. Note that this ransomware creates five registry strings and one of them at HKCU\Software\Microsoft\Windows\CurrentVersion\Run whose value data should be %AppData%\{RANDOM CLSID}\randomlynamed.exe is set to run Cerber2 Ransomware on each system boot up.
Our malware analysts have found that this ransomware is configured to encrypt close to 400 file formats, so any documents, pictures and other important information you may have will be encrypted using AES-256. It will generate a private decryption key and encrypt it with an RSA-576 encryption algorithm. The names of the encrypted files will be appended with the .cerber2 encryption. After a successful encryption, the ransomware will generate three files that include, DECRYPT MY FILES.txt, DECRYPT MY FILES.html, and DECRYPT MY FILES.vbs. These files contain information on how to pay the ransom. Testing has shown that this ransomware wants you to pay 1.24 BTC ($522) within seven days, or the ransom will increase to 2.48 ($1044.) However, we do not recommend that you pay the ransom because you might not get the promised Cerber Decryptor. We think that its developers get a cut of the profits made the “clients” that use Cerber2 Ransomware to encrypt your files. Therefore, by paying the ransom, you will finance the development of new malware.
We advocate for the removal of Cerber2 Ransomware because paying the ransom is not a viable option. You might not receive the decryptor, or it might not work. Furthermore, paying the ransom can be a waste of money especially since the criminals want to you pay from $522 to $1044. So if you have made the decision to delete this ransomware, then consult the instructions at the end.
Boot the PC in Safe Mode with Networking
Windows 10
- Click the Start button and then the Power button.
- Hold down the Shift key and select Restart.
- In the resulting, full-screen menu, select Troubleshoot.
- Select Advanced options and click Startup Settings.
- In the Startup Settings screen, press Restart.
- The PC will reboot and bring you to a Startup Settings screen.
- Select Enable Safe Mode with Networking.
Windows 8 & 8.1
- Hold down the Windows+C keys, and then click Settings.
- Click Power, hold down Shift on your keyboard and click Restart.
- Click Troubleshoot.
- Select Advanced options, and select Startup Settings.
- Click Restart and press 5 on your keyboard to Enable Safe Mode with Networking.
Windows 7 & Vista
- Click the Start button and click the arrow next to the Shut Down button.
- Then, click Restart.
- Press and hold the F8 key as your computer restarts.
- On the Advanced Boot Options screen, use the arrow keys to highlight the Safe Mode with Networking, and then press Enter.
- Log on to your computer with a user account that has administrator rights.
Windows XP
- Click the Start button and then click Restart.
- Press and hold the F8 key as your computer restarts.
- On the Advanced Boot Options screen, use the arrow keys to highlight the Safe Mode with Networking, and then press Enter.
- Log on to your computer.
Removal Guide
- Simultaneously press Windows+E keys.
- In the File Explorer, enter the following file paths.
- %ALLUSERSPROFILE%\Start Menu\Programs
- %APPDATA%\Microsoft\Windows\Start Menu\Programs
- %USERPROFILE%\Microsoft\Windows\Start Menu\Programs
- %ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs
- %ALLUSERSPROFILE%\Application Data\Microsoft\Windows\Start Menu\Programs
- Find randomname.Ink and delete it.
- Go to %AppData% and locate the {RANDOM CLSID} folder.
- Enter it and delete the randomname.exe
Delete the registry keys
- Simultaneously press Windows+R keys.
- Enter regedit in the dialog box and hit Enter.
- In the Registry Editor, navigate to the following registry keys.
- HKCU\Software\Microsoft\Command Processor\AutoRun
- HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\RunCLSID}\*.exe"
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce
- Locate the randomly named registry key featuring the Value data {RANDOM CLSID}\randomlynamed.exe
- Right-click it and click Delete.
- Then go to HKCU\Control Panel\Desktop
- Locate SCRNSAVE.EXE and delete it.
In non-techie terms:
Cerber2 Ransomware is a newer version of the infamous Cerber Ransomware. Not much has changed since the first release, but this ransomware is as dangerous as ever. It is set to encrypt your personal files and demand that you pay a ransom for the decryption key that costs a substantial sum of money. However, we recommend that you delete it instead using the guide above or our SpyHunter — our recommended anti-malware tool.
