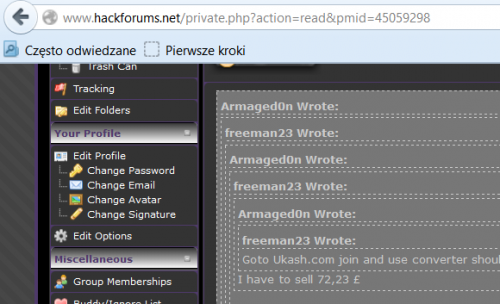
Polish Police in cooperation with the Belgian Federal Police and Europol arrested a Polish citizen Tomasz T., who uses the nickname Armaged0n at Hack Forums (https://hackforums.net), on the 14th of March, 2018. The arrest took place in Opole, Poland while Tomasz was visiting his homeland. Authorities had been tracking him for years, but he was hiding in Belgium, so a few years passed until they managed to arrest him. The suspect faces 181 charges, including computer fraud and money laundering, and he has already pleaded guilty, authorities reported. It seems that Tomasz earned more than $145 000 from performing various cybercrime, including spreading Polski Ransomware, Flotera Ransomware, and Vortex Ransomware, between 2013 and 2018. The aforementioned ransomware infections were used as tools to obtain money from various Polish companies mainly, but it is very likely that some individual computer users worldwide became victims of these nasty infections too.
It is believed that Tomasz started his “career” back in 2013. He did not use any ransomware infection to obtain easy money at first. Instead, he used a banking Trojan to earn some money illegally. To be more specific, this Trojan infection was designed to replace bank account numbers in users’ clipboards with the one belonging to the attacker. As a consequence, Tomasz could receive all affected users’ bank transfers. Most probably, this was not enough for him because he shifted to developing and using ransomware infections for money extortion at the beginning of 2017.
Its first creation was Polski Ransomware in January 2017. As its name suggests, it targeted users/companies in Poland. This threat was programmed to encrypt victims’ photos, invoices, database copies, and other important files with AES-256. After encryption, all affected files were marked with the .aes256 filename extension. Just like similar ransomware-type infections, it was developed to obtain money, so it asked victims to pay $249 to the author in exchange for the decryptor.
The second ransomware infection Tomasz developed in March 2017 was Vortex Ransomware. It should be emphasized that this threat remained active until the beginning of 2018. It also used the AES-256 encryption method to encrypt victims’ files. Unlike Polski Ransomware, it used to append .aes to locked data. Also, the amount of money it demanded was smaller ($199) if compared to the size of the ransom asked by Polski Ransomware, but the reason it was released was surely the same – to extract money from victims easier.
Finally, at the end of March 2017, Flotera Ransomware was released. It was also developed having only one purpose in mind – to get easy money. Therefore, like other ransomware infections released by Tomasz, it encrypted files right away after infiltrating victims’ computers and then demanded a ransom ($199).
Malicious applications developed by Tomasz were mainly distributed via emails. Specifically speaking, victims received “important” emails from such well-known companies as DHL, WizzAir, Zara, and others. Once the attachment inside the malicious email was opened, malware was dropped on the user’s computer and started performing malicious activities immediately.
Even though Tomasz is best known for developing malware and using it to make a profit, it is responsible for other cybercrime too. For example, it seems that he conducted DDOS attacks and actively spread banking Trojans. On top of that, Polish Police suspect that Tomasz could make around $20 000 in November 2017 by simply buying and selling Bitcoin received from ransomware victims online.
Following the suspect arrest, police took the computer and other equipment belonging to Tomasz from his apartment in Belgium. Specialists managed to access information stored on the machine and remote servers. As a consequence, they are now in possession of all decryption keys too, meaning that files locked by any ransomware infection developed by Armaged0n can be unlocked for free. Specialists encourage victims to contact the nearest police station to get the decryptor.
References:
- Balaji, N. 3 Dangerous Ransomware Families Author Arrested in Poland and Seized the All Decryption Keys. GBHackers on Security
- Cimpanu, C. Author of Polski, Vortex, and Flotera Ransomware Families Arrested in Poland. BleepingComputer
- Free stock photos. Pexels
- Goud, N. Polish Cops arrest the author of Polski, Vortex and Flotera Ransomware. Cybersecurity Insiders.
- SC Staff. Newsbite: Polish police arrest prolific ransomware cyber-criminal. SC Media
- Walker, J. Suspected ransomware mastermind arrested in Poland. The Daily Swig