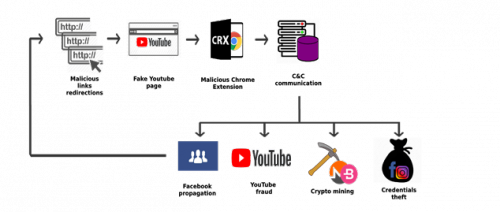
Facebook users have always been one of the major cyber criminals’ targets, so it is not surprising that new Facebook malware campaigns are launched from time to time. The newest malicious campaign was detected on the 3rd of May, 2018 by Radware. To be more specific, Radware researchers discovered a new malicious application which was dubbed Nigelthorn. It is definitely not the first malicious application targeted at Facebook users, but we have to admit that it is quite unique. As observed by specialists who carried out an analysis, Nigelthorn malware mainly spreads via socially-engineered links on Facebook. What else makes it an interesting piece of software is the fact that it abuses a Google Chrome extension called Nigelify. This explains why this malicious application was dubbed Nigelthorn. Unfortunately, it stayed undetected for some time. According to specialists, the chances are high that it has been active since March, 2018. As a consequence, it has already managed to infect more than 100, 000 users in, at least, 100 countries. Why was it so difficult to detect it? There are, basically, two reasons. First, the malicious campaign changes extensions it uses periodically. Second, it uses an advanced evasive mechanism to spread malware undetected. We would lie if we said that this is something completely new because researchers already know about two similar operations: facexworm and digimine.
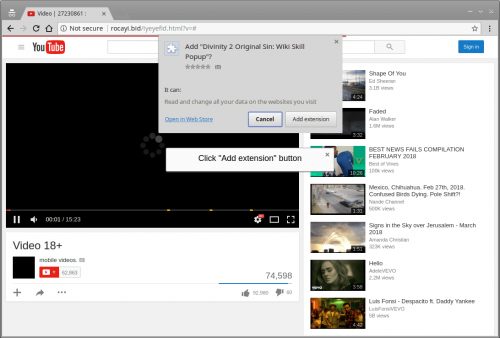
As in the case of older Facebook malicious campaigns, all problems begin when users click on malicious links sent to them. If the link is clicked, a fake YouTube page is opened and then users are asked to install a Chrome extension, typically Nigelify, to watch the video. It should be emphasized that this malicious campaign primarily targets Google Chrome users. According to them, users who use other web browsers should be safe. Once the Add Extension button is clicked, the malicious extension is installed on the system and, consequently, the computer becomes a part of the botnet. Additionally, a set of plugins, each with a different malicious purpose, is automatically downloaded from C2 (command-and-control server). According to statistics, the majority of Facebook users affected by Nigelthorn malware live in Philippines, Venezuela, and Ecuador.
Surprisingly, legitimate Chrome extensions are used by malicious campaign operators. They simply inject an obfuscated malicious script in them. Researchers at Radware say that this is, most probably, done to bypass the extension validation procedure. At the time of writing, there were several extensions that were possibly involved in the malicious Facebook campaign known to malware analysts: Nigelify, PwnerLike, Alt-j, Fix-case, Divinity 2 Original Sin: Wiki Skill Popup, keeprivate, and iHabno.
We have to admit that Nigelthorn is an example of sophisticated malware. Let’s analyze what it is capable of. First, it can steal Facebook login credentials and Instagram cookies. If this information is found on the affected machine, it is immediately sent to C2. Once malware gets access to Facebook, it starts collecting relevant account information and then spreading malicious links. They are usually spread via Facebook Messenger, or users may find themselves tagged to posts containing the malicious link together with other 49 contacts. Second, Nigelthorn downloads a crypto-mining tool from its server. In other words, the affected machine’s resources (CPU power) are used to mine various cryptocurrencies. As a consequence, a dramatic decrease in the affected computer’s speed can be noticed. As analysis showed, cyber criminals managed to mine 1000 USD over 6 days.
There is no doubt that Nigelthorn malware is extremely persistent. That is, it does not want to be removed. Because of this, it closes the extension tab immediately if it is opened by the user. In other words, it tries to prevent the removal of the extension with the malicious code. Additionally, it might block Facebook and Chrome cleanup tools. In some cases, Facebook users might notice that they can no longer edit/delete posts and write comments.
It is not very likely that no new malicious applications targeting Facebook users will be released ever again, so it is necessary to take security measures to avoid serious security-related problems. Since users are usually the ones responsible for allowing malicious software to enter their systems, you should change your habits too. First of all, start by always inspecting links you are about to click. Not all harmless-looking links are really decent, so double-check those that look legitimate at first glance too. Second, it would be a good idea to keep a security application installed on the system.
References:
- Radware. Nigelthorn Malware Abuses Chrome Extensions to Cryptomine and Steal Data. Radware Blog
- Free stock photos. Pexels