Do you know what Asasin Ransomware is?
According to our cybersecurity experts, Asasin Ransomware can infect your PC by stealth and encrypt your files. Once your files have been encrypted, this program will demand that you pay a ransom to decrypt them. However, you should not pay the ransom because it is likely that the cybercriminals will not send you the decryption key/tool, and remove it instead. We recommend waiting for a free decryption tool to be released by the cybersecurity industry, but there is no guarantee. For more details on this infection, please read this whole article.
Let us discuss how Asasin Ransomware might be distributed. According to our researchers, it is likely that this program’s developers employ malicious emails to get this ransomware onto the computers of unsuspecting users. The emails can be sent from a dedicated email server atdocuments@rightsignature.com and can be disguised as emails from legitimate companies. It is most likely that the emails will have the executable of this ransomware attached. However, it might be zipped, so if you open the file archive and run the executable inside, then your PC can become infected with this ransomware. If you choose to run the file without downloading it, then it will be downloaded as a temporary file to %TEMP% folder, but it might remain there. The emails can be disguised as invoices or receipts, and that attached ransomware file can pose as a PDF or MS Word document. The email text can convince you to open the attached file and, if you do, then it will be too late. If you do not have an anti-malware program, then this ransomware will start doing its dirty work.
Once on your computer, Asasin Ransomware is set to begin encrypting your files. Researchers say that this ransomware might use the RSA-2048 and AES-128 encryption algorithms. If this is true, then the encryption method used is very strong indeed and creating a free decryption tool may take some time (if it will be created at all.) While encrypting your files, this ransomware appends the encrypted files with an “.asasin” file extension. It was also configured to rename the encrypted files. The renaming pattern used is [8 characters]-[4 characters]-[4 characters]-[8 characters]-[12 characters].asasin. The name is a combination of the user's ID and random characters, and the first three sections are the user’s ID. This ransomware drops an image file named asasin.bmp on the desktop and replaces the desktop background image with it. Furthermore, it drops a file named asasin.htm on the desktop as well, and both of these files contain the same ransom note text. Researchers say that the developers of this ransomware want you to pay 0.25 BTC which is an approximate 1400 USD, and it is a lot of money.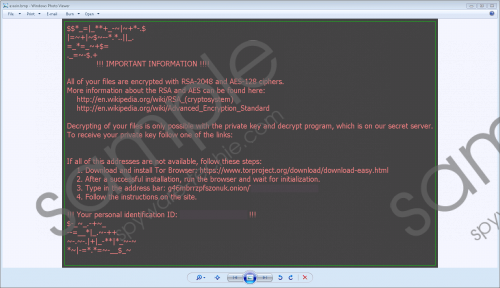 Asasin Ransomware screenshot
Asasin Ransomware screenshot
Scroll down for full removal instructions
As you can see, Asasin Ransomware is one dangerous computer infection that can encrypt your most valuable files and demand you pay money to get them decrypted. However, you should not trust cybercriminals to hold their end of the bargain. Therefore, we recommend that you remove this ransomware instead. We suggest using SpyHunter’s free malware scanner to find the malicious file for you so that you could go to its location and delete it manually.
Removal Guide
- Go to http://www.spyware-techie.com/download-sph
- Download SpyHunter-Installer.exe
- Install the program and run it.
- Click Scan Computer Now!
- Copy the file path of the malware from the scan results.
- Press Windows+E keys.
- Enter the file path of the malware in File Explorer’s address box.
- Press Enter.
- Locate and right-click the malicious file(s) and click Delete.
- Delete asasin.bmp and asasin.htm from the desktop.
- Empty the Recycle Bin.
In non-techie terms:
Asasin Ransomware is one highly malicious computer infection that can encrypt your files in order to compel you to buy a decryption tool/key from this ransomware’s developers. You should not pay the ransom because the cybercriminals can trick you and not send you the decryptor, so you can just remove it.
