Do you know that AES-NI Ransomware is?
Ransomware is the kind of malware that takes something hostage in the hopes of making money. The malicious AES-NI Ransomware takes hostage your files by encrypting them. It is suggested that in order to get a private RSA key, you need to email the cyber criminals who have created the infection. Would you be provided with a decryption key after you emailed them? Of course, you would not. Cyber crooks need you to initiate communication so that they could demand a ransom, and it could be extremely big. Unfortunately, it is unlikely that a decryptor would become available even if you paid the ransom, and so it does not matter whether it is big or small. Unfortunately, that means that it might be impossible for you to get your files back. Whether or not that is the case, you must remove AES-NI Ransomware from your Windows operating system, and you need to do that as soon as possible.
The distribution of AES-NI Ransomware is mysterious. While most ransomware threats – including the latest ones, FileFrozr Ransomware and Jeeperscrypt Ransomware – spread via spam emails, this threat could enter in a different manner. According to our research team, the infection could be manually installed using RDP brute-force attacks. The Doublepulsar backdoor could be employed as well. All in all, though different methods could be employed to infiltrate AES-NI Ransomware, it always acts the same. First and foremost, it encrypts files. If you do not know which files on your operating system were encrypted, look for the “.aes_ni_0day” extension. Every folder containing the encrypted files should also contain a file called “!!! READ THIS - IMPORTANT !!!.txt”. This file represents the demands that the creator of the ransomware has for you. The first thing you are asked to do is contact one of the emails (0xc030@protonmail.ch, 0xc030@tuta.io, or aes-ni@scryptmail.com).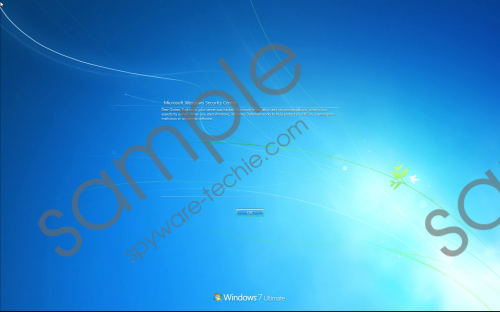 AES-NI Ransomware screenshot
AES-NI Ransomware screenshot
Scroll down for full removal instructions
The so-called “RSA private key” might be promised to you in return for a specific fee, which you are likely to be introduced to when you email the creator of AES-NI Ransomware. You are also given the option to communicate with them via BitMsg. The ransom note also warns against using third-party file decryption tools or employing “data recovery companies.” These warnings are added just so that you would pay the ransom quicker. Unfortunately, all the promises in the world could not guarantee that the transaction (a working decryptor in return of money) would be fair, and that is why paying the ransom or following any other demands is not recommended. If you are one of the cautious users who have all personal files backed up, you do not need to worry about any of this. The only thing you should take care of is the removal AES-NI Ransomware. Note that as long as the threat is active, you will be facing the fictitious “Microsoft Windows Security Center” message when you start your computer.
If you follow the manual removal instructions presented below, you will delete AES-NI Ransomware manually. Unfortunately, not all users will be able to identify the launcher file with the unknown name, in which case, it is best to utilize anti-malware software. Do not hesitate to use this software because it can eliminate existing threats in the most efficient manner, and, more importantly, it can provide you with full-time protection, which is what you need if you wish to guard yourself against malware in the future. After you delete the ransomware, you also need to figure a way to back up your personal files; that is, if you have no taken care of this already.
Remove AES-NI Ransomware
N.B. The launcher file is likely to be removed after the encryption, but you should scan your operating system to see if it exists anyway.
- Identify the {unknown name}.exe launcher file.
- Right-click and Delete it.
- Launch RUN by tapping Win+R keys on the keyboard.
- Enter regedit.exe into the dialog box and click OK.
- In the Registry Editor move to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon.
- Right-click and Delete the value named LegalNoticeText.
- Perform a full system scan to check for any leftovers.
In non-techie terms:
Every user facing the malicious AES-NI Ransomware knows that it requires removal; however, many of them postpone the operation because their files are taken hostage. The ransomware encrypts the files using a complicated algorithm, and then it pushes the victim to contact cyber criminals using one of the provided emails (or using BitMsg). Needless to say, the creator of the ransomware wants money, and as soon as you contact them, they will instruct you to pay a ransom. Since a decryption key is unlikely to become available after you pay money, that is not recommended. Removing the ransomware is extremely important, and you can do that using anti-malware software. If you do not care about further system’s protection, you can stick with manual removal, which is represented via the guide below.
